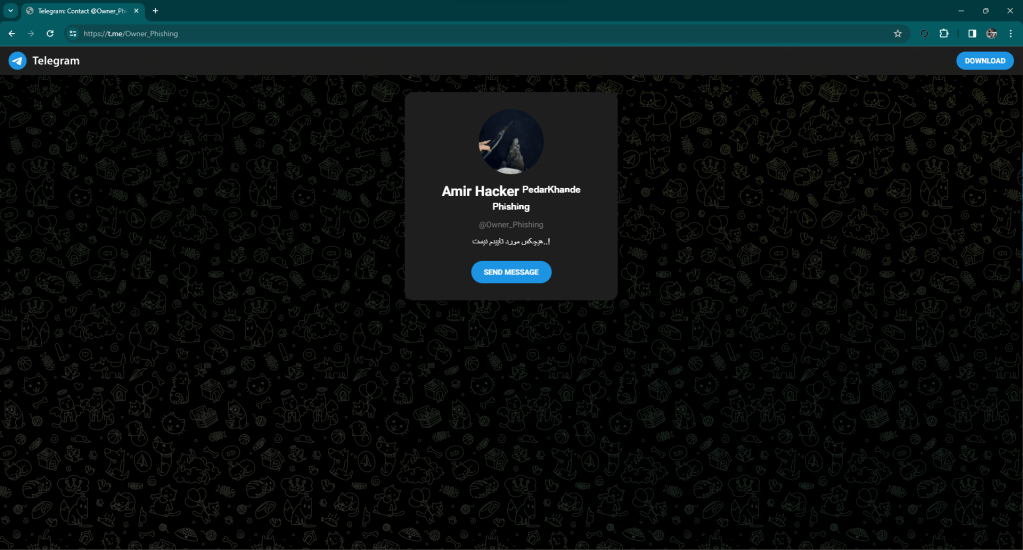
A little while ago I came across this website: hxxps://domin-remote[.]online
The domain was registered yesterday via hostinger. To date it has not been reported.
Matrix reported it on urlscan.io 15 hours ago.
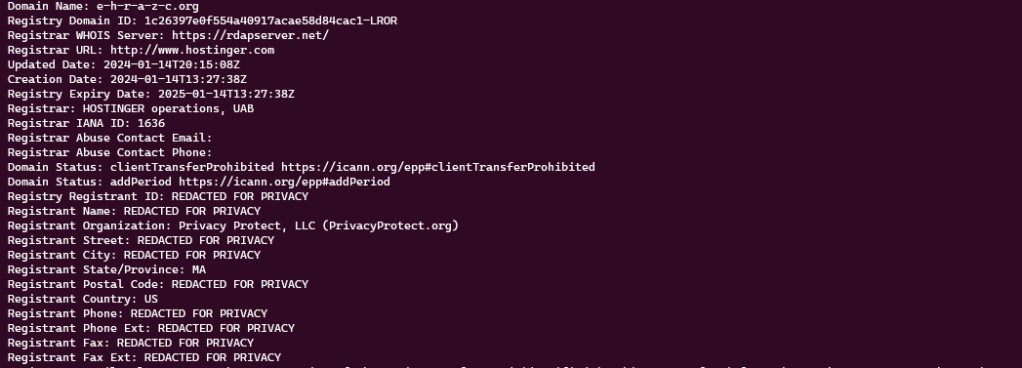
Domain Name: DOMIN-REMOTE.ONLINE
Registry Domain ID: D424887618-CNIC
Registrar WHOIS Server: whois.hostinger.com
Registrar URL: https://www.hostinger.com/
Updated Date: 2024-01-15T10:57:55.0Z
Creation Date: 2024-01-15T10:57:50.0Z
Registry Expiry Date: 2025-01-15T23:59:59.0Z
Registrar: HOSTINGER operations, UAB
Registrar IANA ID: 1636
Domain Status: serverTransferProhibited https://icann.org/epp#serverTransferProhibited
Domain Status: clientTransferProhibited https://icann.org/epp#clientTransferProhibited
Domain Status: addPeriod https://icann.org/epp#addPeriod
Registrant Organization: Privacy Protect, LLC (PrivacyProtect.org)
Registrant State/Province: MA
Registrant Country: US
Registrant Email: Please query the RDDS service of the Registrar of Record identified in this output for information on how to contact the Registrant, Admin, or Tech contact of the queried domain name.
Admin Email: Please query the RDDS service of the Registrar of Record identified in this output for information on how to contact the Registrant, Admin, or Tech contact of the queried domain name.
Tech Email: Please query the RDDS service of the Registrar of Record identified in this output for information on how to contact the Registrant, Admin, or Tech contact of the queried domain name.
Name Server: NS6.NL.HOSTSAILOR.COM
Name Server: NS5.NL.HOSTSAILOR.COM
DNSSEC: unsigned
Billing Email: Please query the RDDS service of the Registrar of Record identified in this output for information on how to contact the Registrant, Admin, or Tech contact of the queried domain name.
Registrar Abuse Contact Email: domains@hostinger.com
Registrar Abuse Contact Phone: +370.68424669
URL of the ICANN Whois Inaccuracy Complaint Form: https://www.icann.org/wicf/
>>> Last update of WHOIS database: 2024-01-16T17:42:53.0Z <<<
For more information on Whois status codes, please visit https://icann.org/epp
>>> IMPORTANT INFORMATION ABOUT THE DEPLOYMENT OF RDAP: please visit
https://www.centralnic.com/support/rdap <<<
The Whois and RDAP services are provided by CentralNic, and contain
information pertaining to Internet domain names registered by our
our customers. By using this service you are agreeing (1) not to use any
information presented here for any purpose other than determining
ownership of domain names, (2) not to store or reproduce this data in
any way, (3) not to use any high-volume, automated, electronic processes
to obtain data from this service. Abuse of this service is monitored and
actions in contravention of these terms will result in being permanently
blacklisted. All data is (c) CentralNic Ltd (https://www.centralnic.com)
Access to the Whois and RDAP services is rate limited. For more
information, visit https://registrar-console.centralnic.com/pub/whois_guidance.
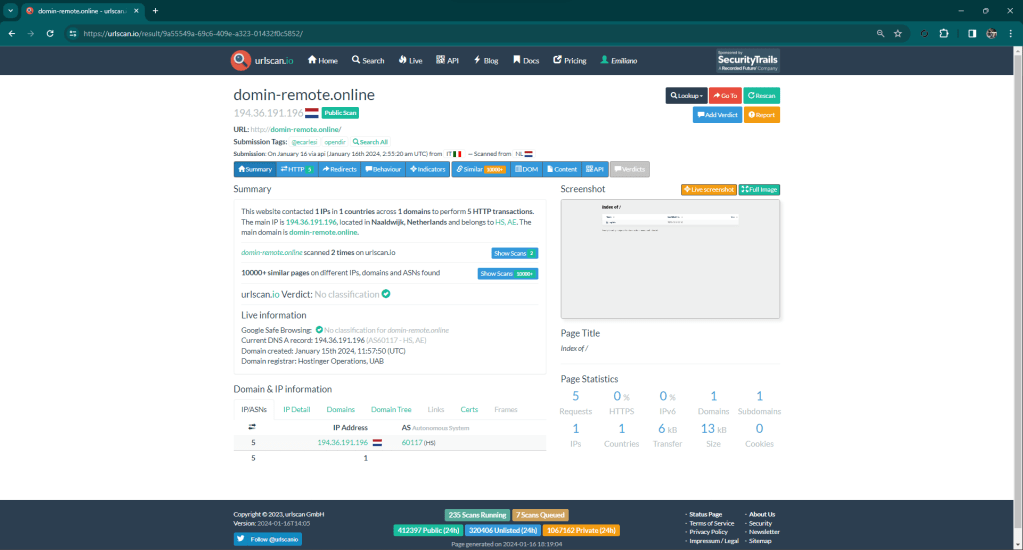
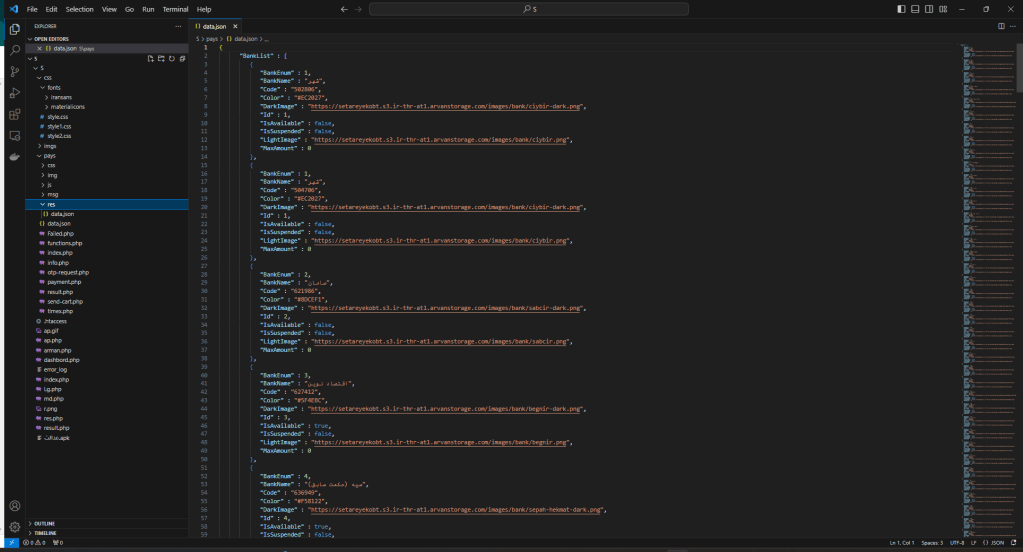
Here you can download the zip file containing everything.
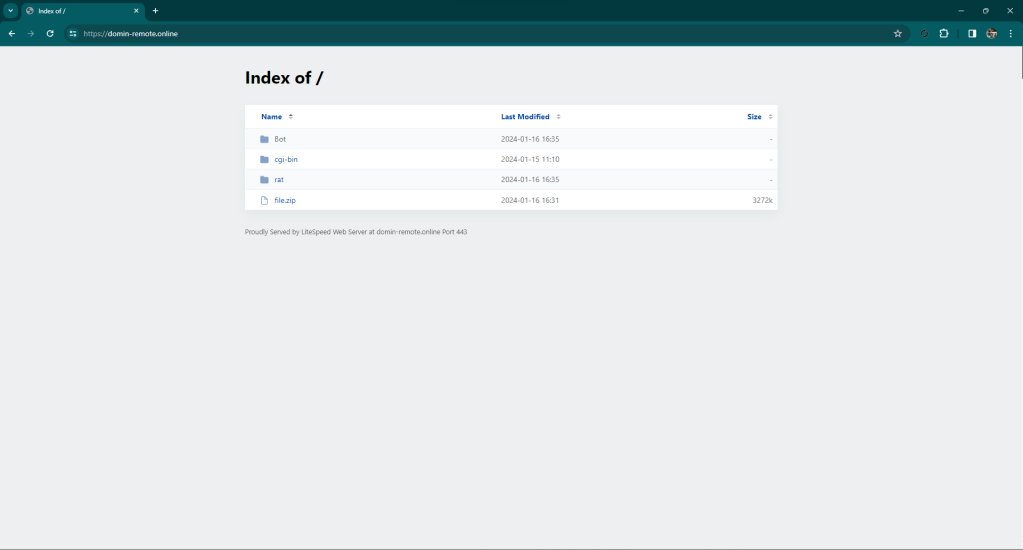
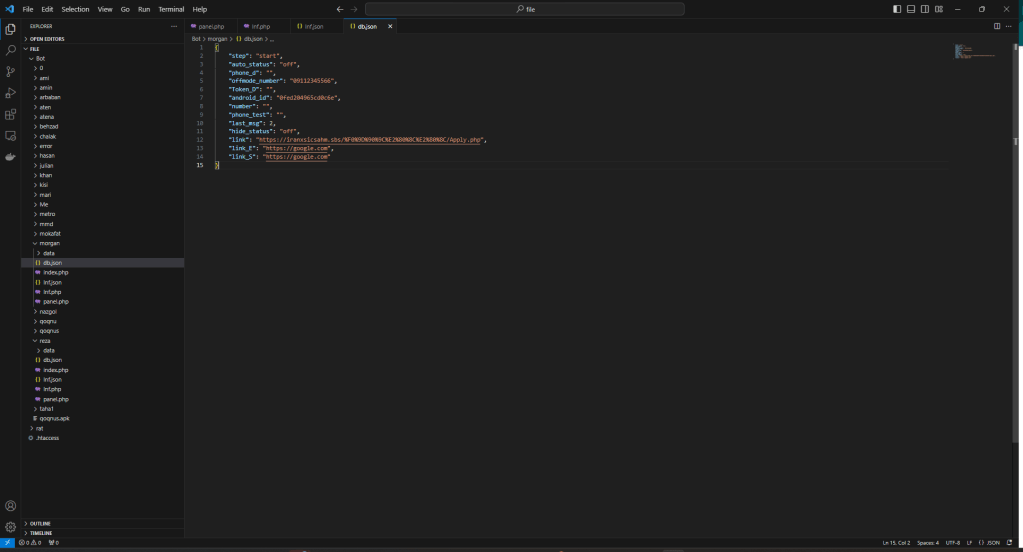
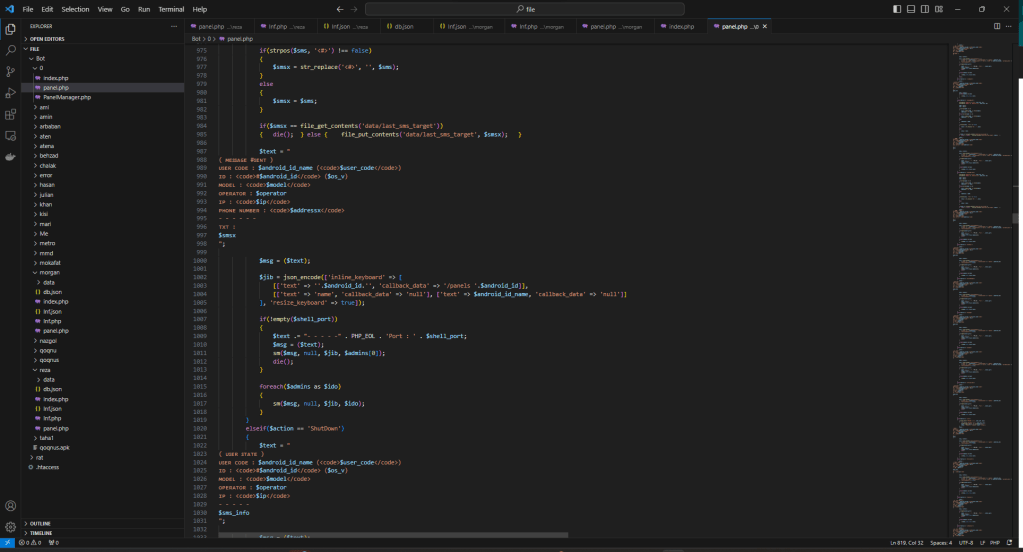
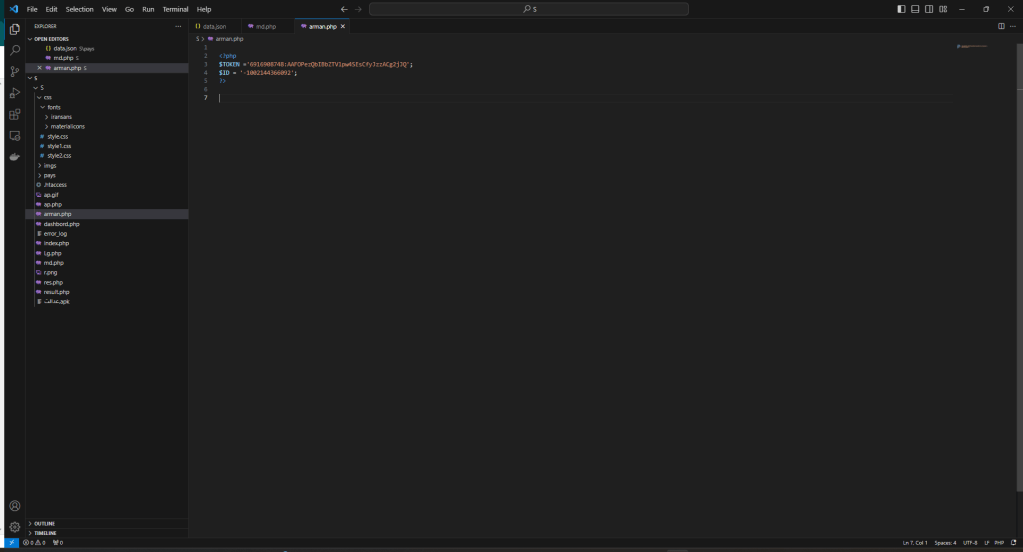
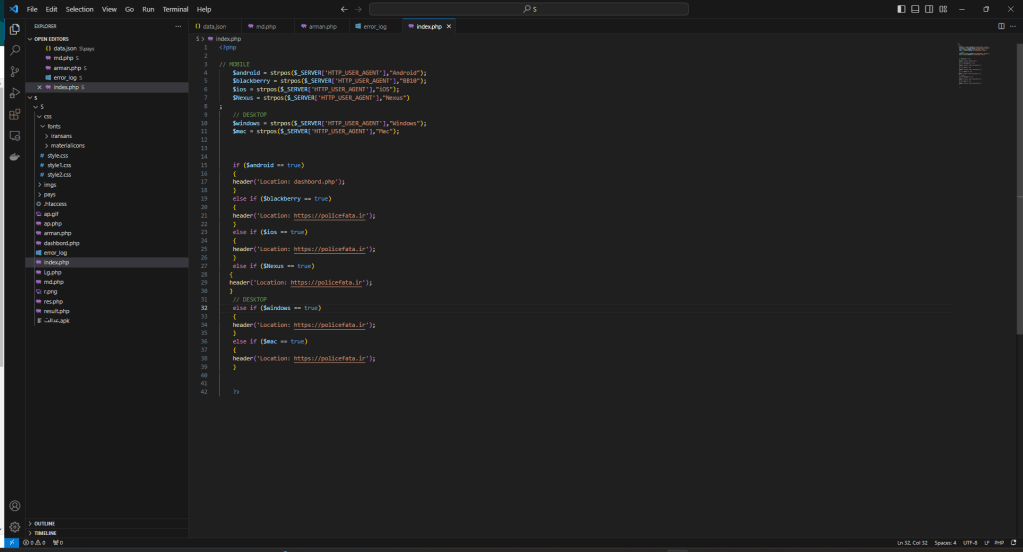
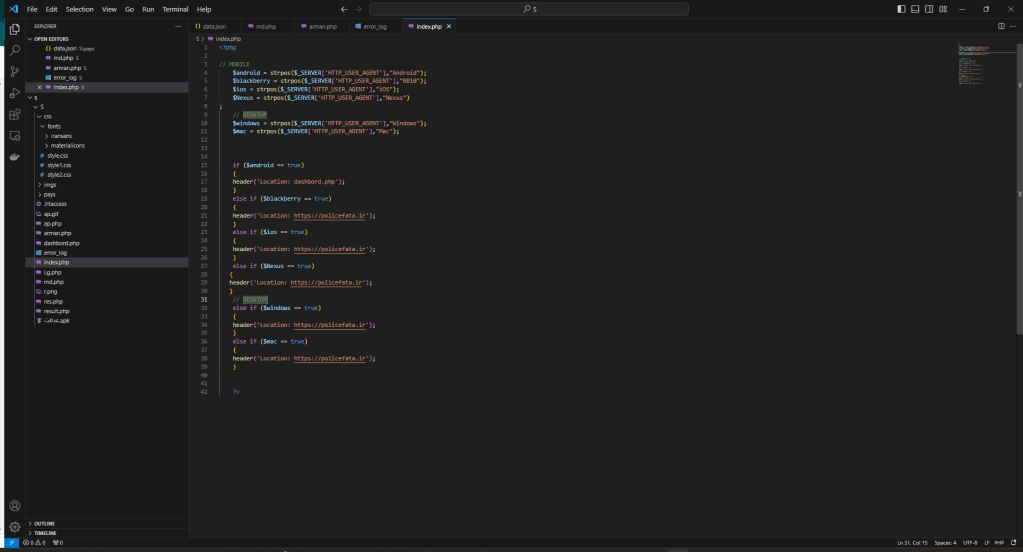
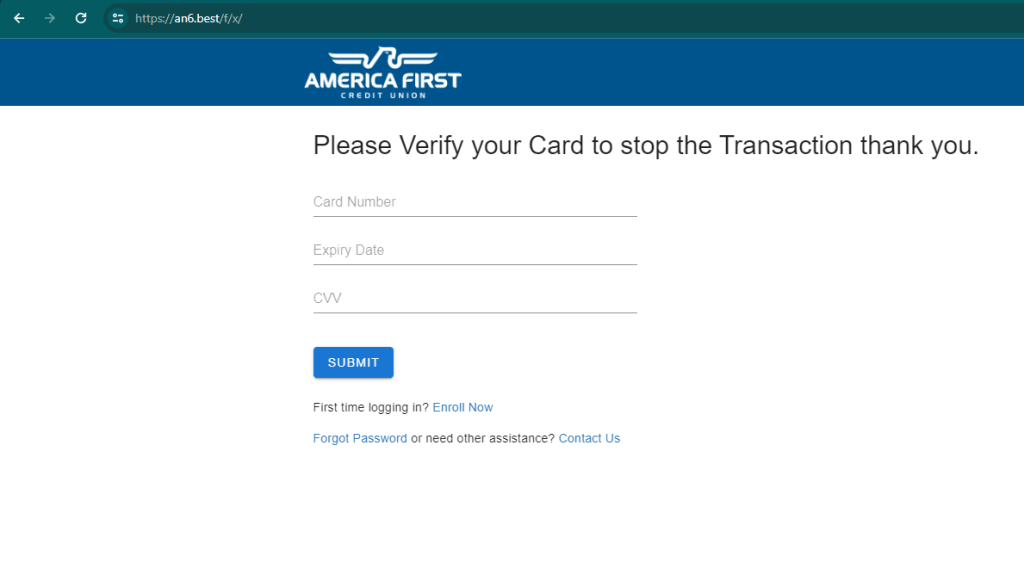
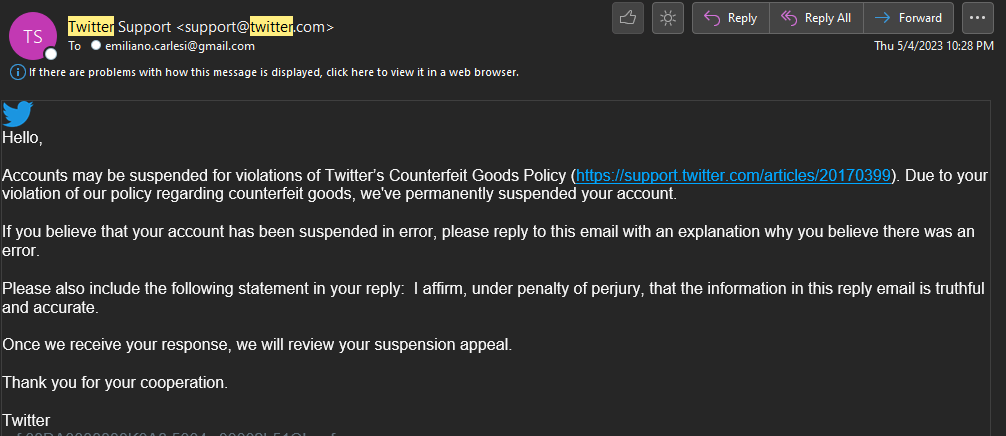
This is the beginning of the attack from which it is possible to download the PHP sources (sorry for “PHP” 😉 ) and the malware for Android, used for the attack.

The malware is a RAT and the sources represent its C2.
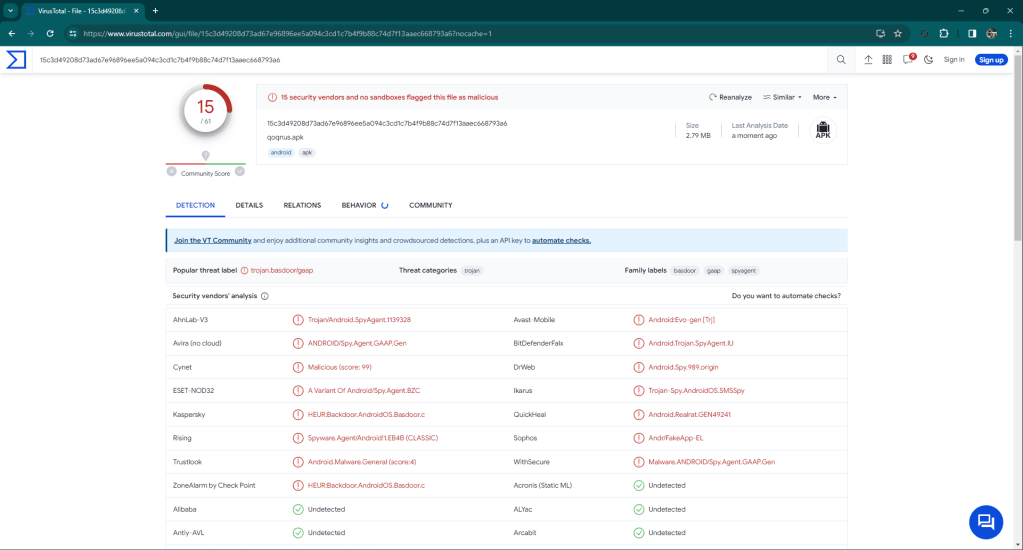
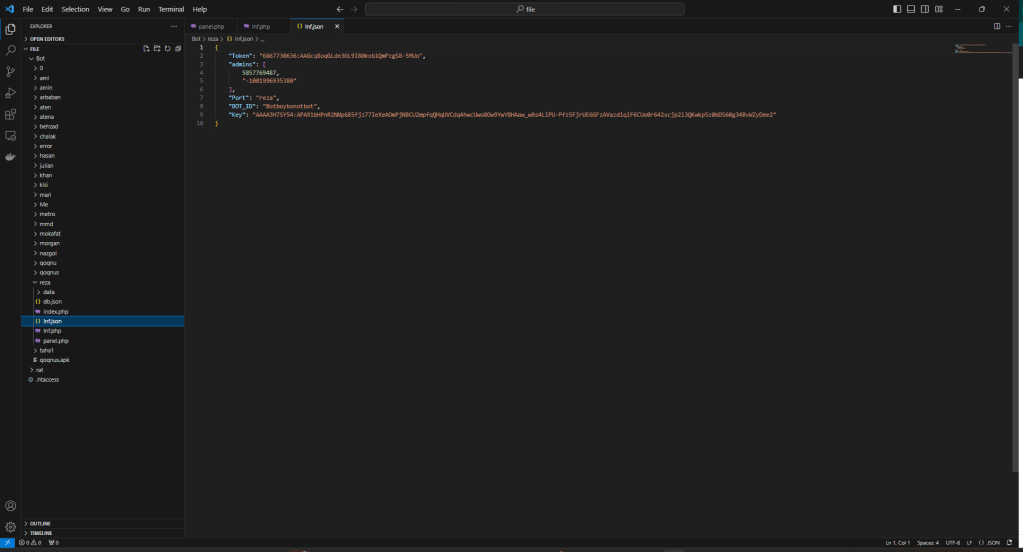
The C2 code is simple and was probably written by a person with little experience, even if he defines himself as a “hacker” while I see him more as a “newbie” with little hope.
Inside you will find everything you need, keys, logs, other domains involved, in short, if anyone has more time than me and wants to find out more, let me know, maybe they could collaborate on this article and enrich it 🙂















You must be logged in to post a comment.