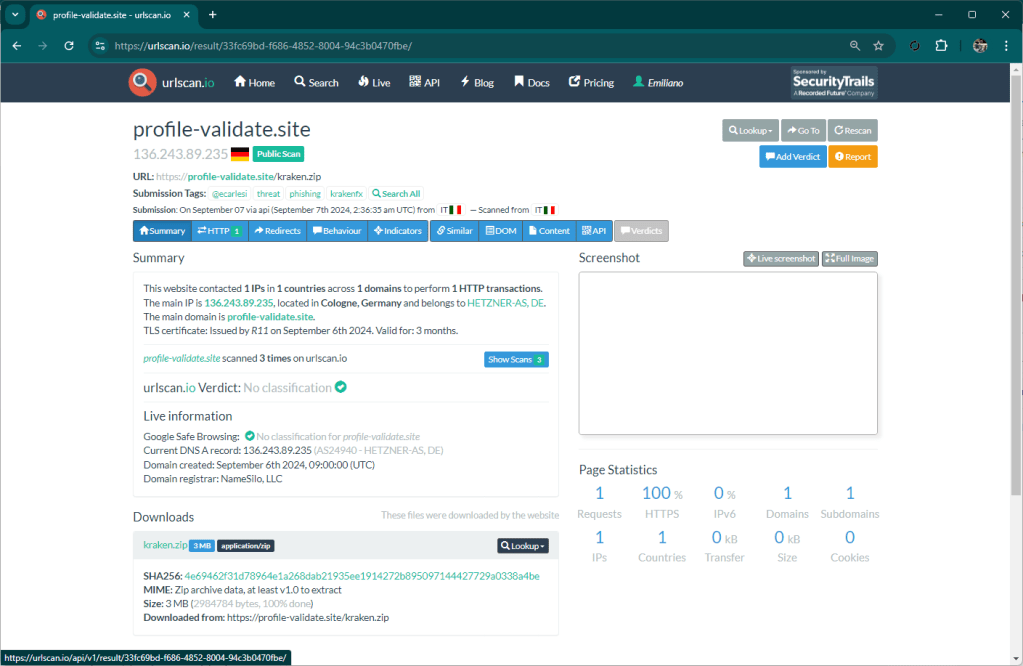
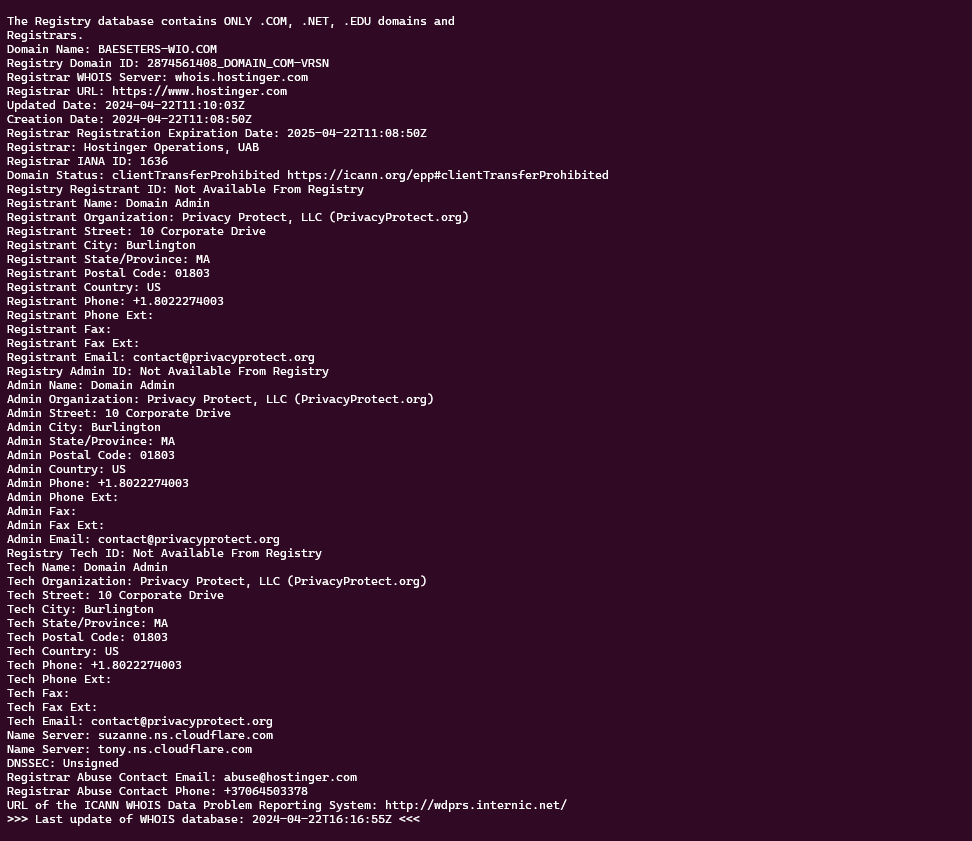
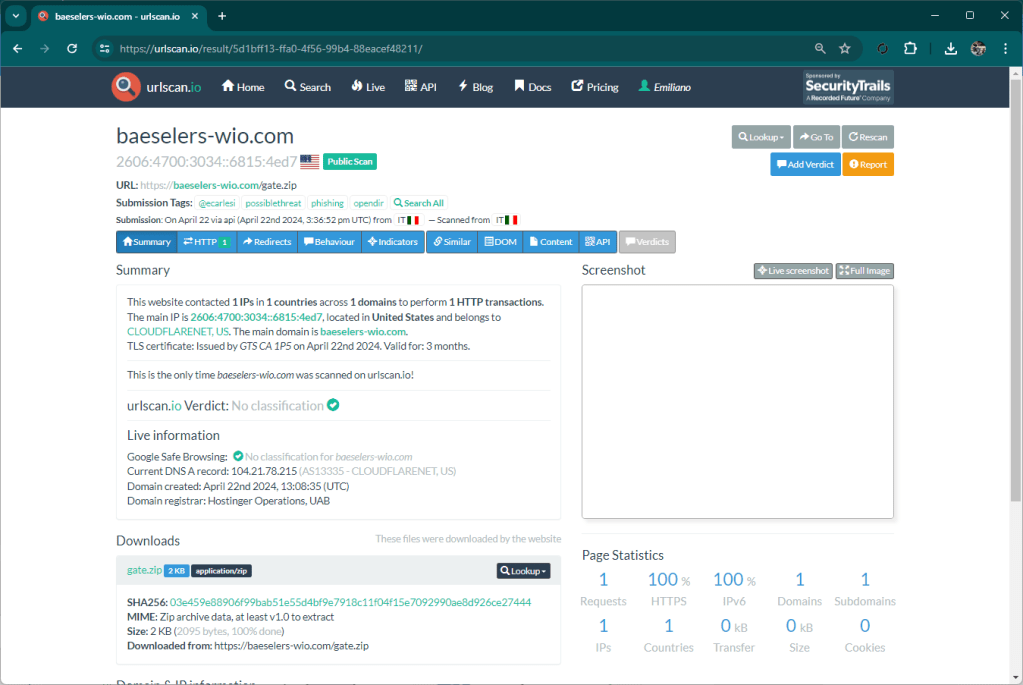
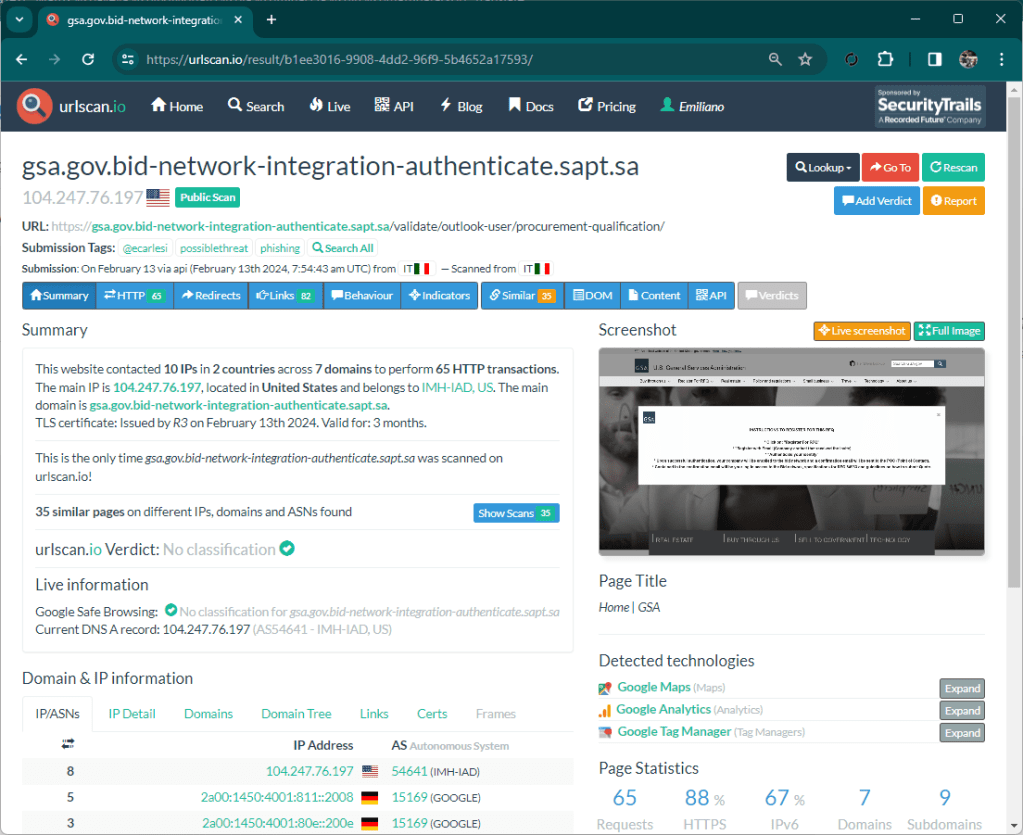
One of the features of Matrix is monitoring on some resources that are detected as suspicious. This monitoring is useful to identify threats like this one I am writing about. An hour ago Matrix reported the site file-share-transfer[.]com as “opendir”, this is because there was no content inside.
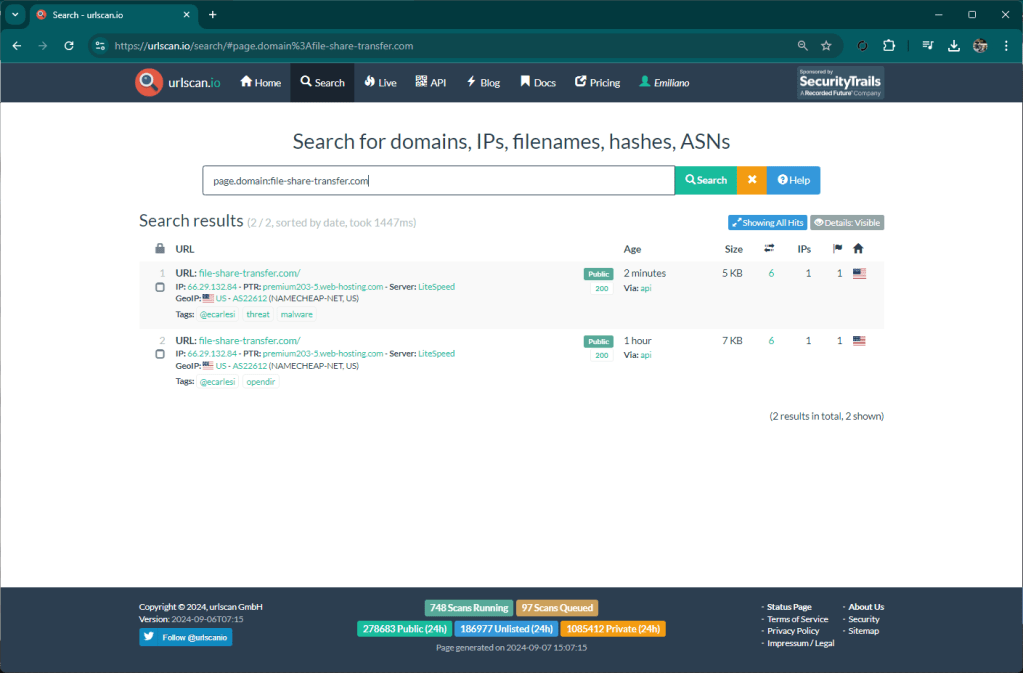
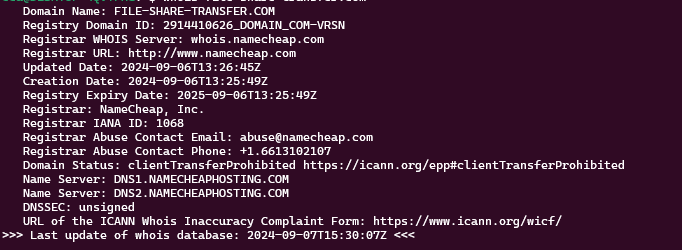
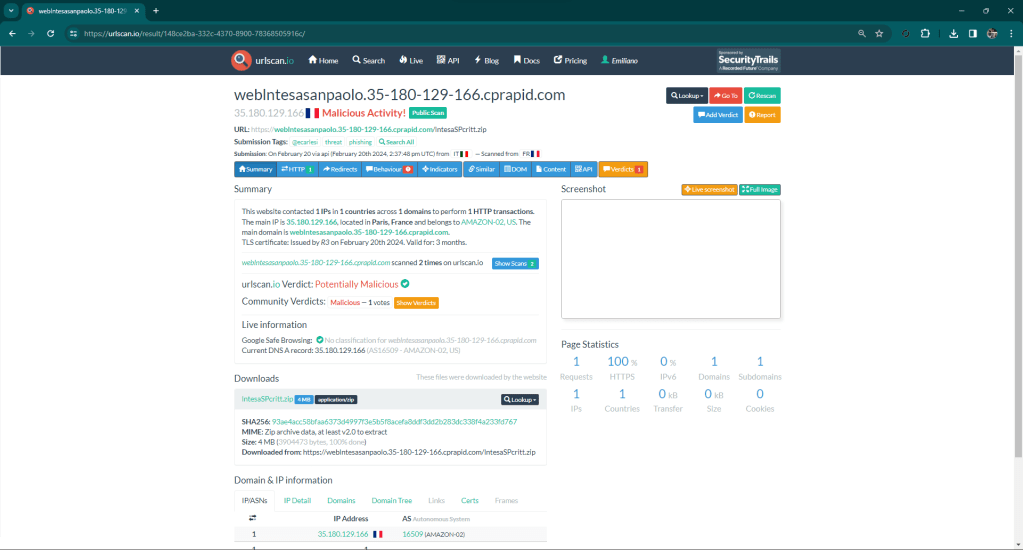
A few minutes ago however the component that monitors the resources already detected, notified an update. Matrix then ran a scan again and detected an active threat.

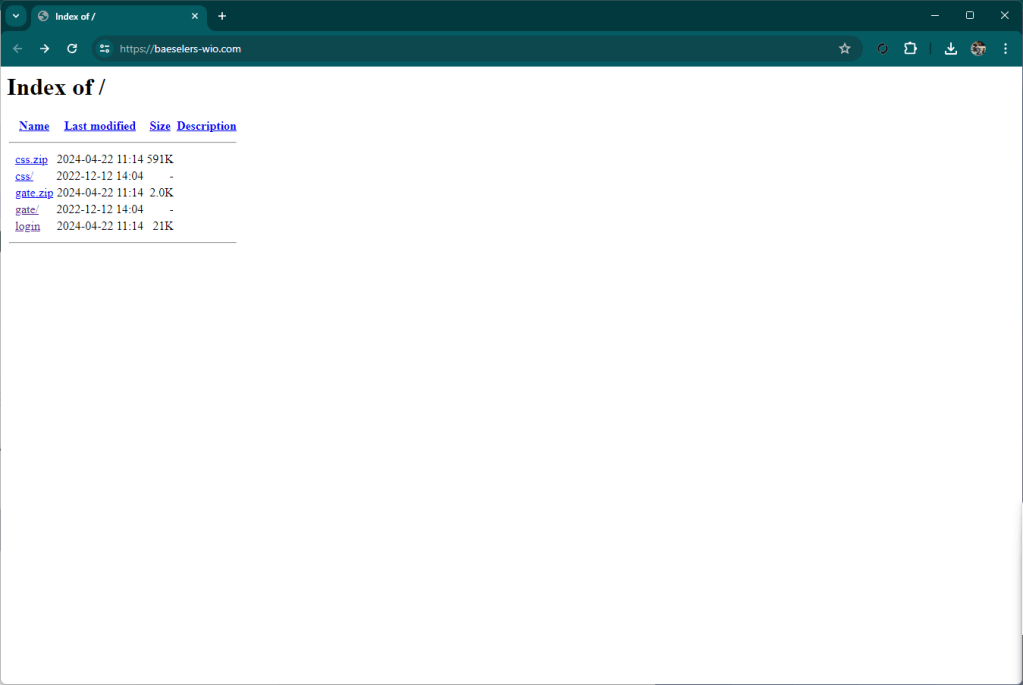
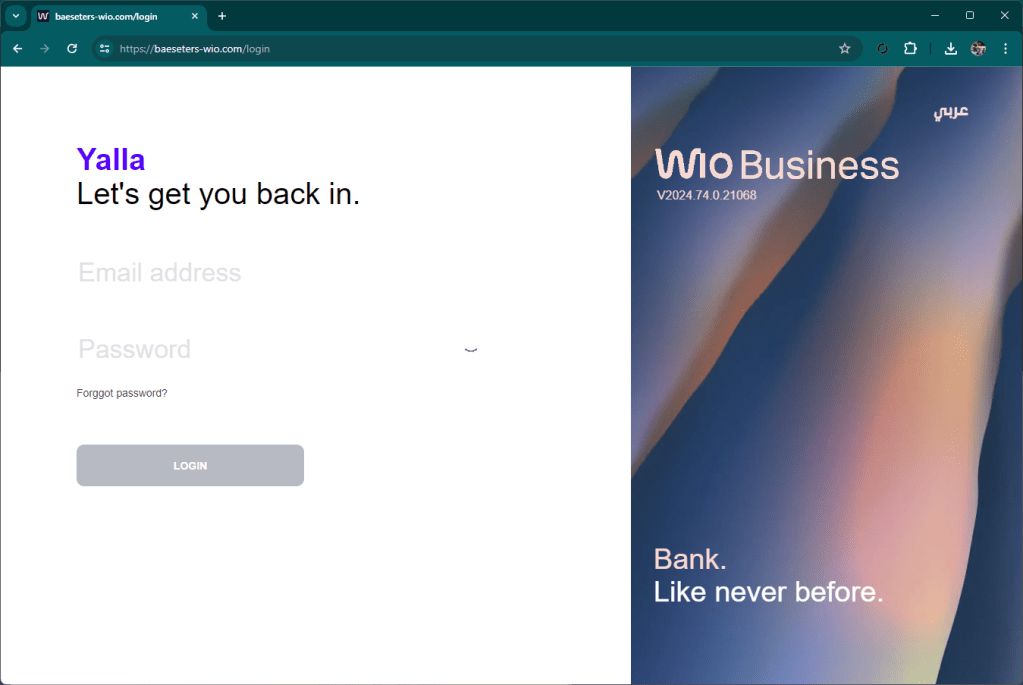
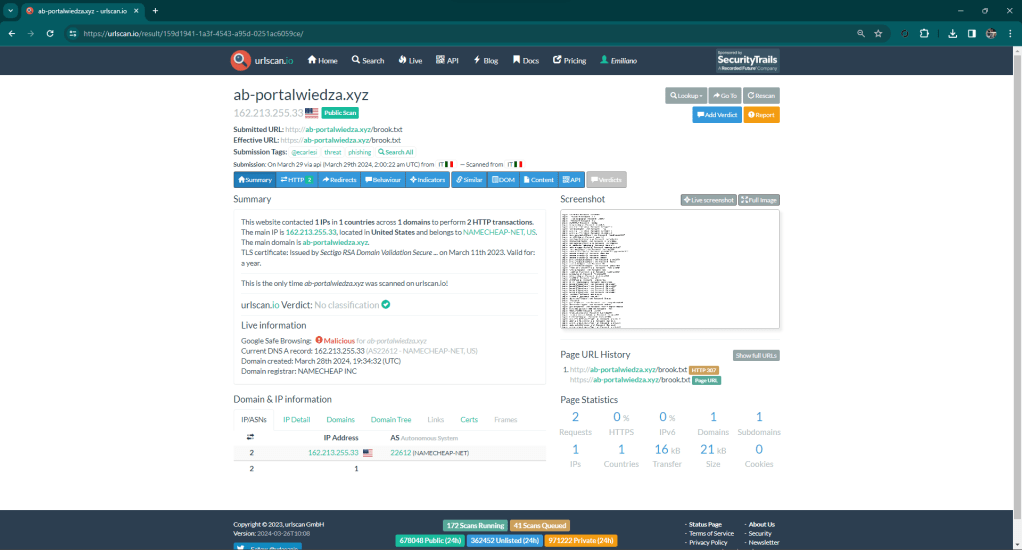
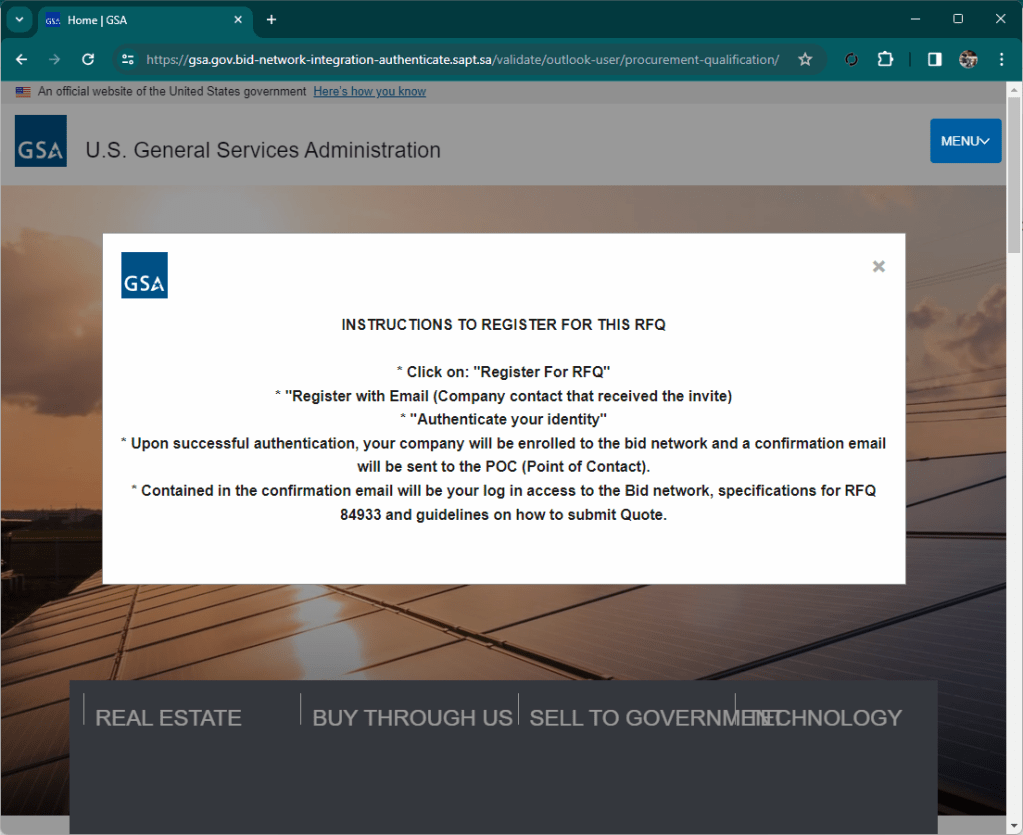
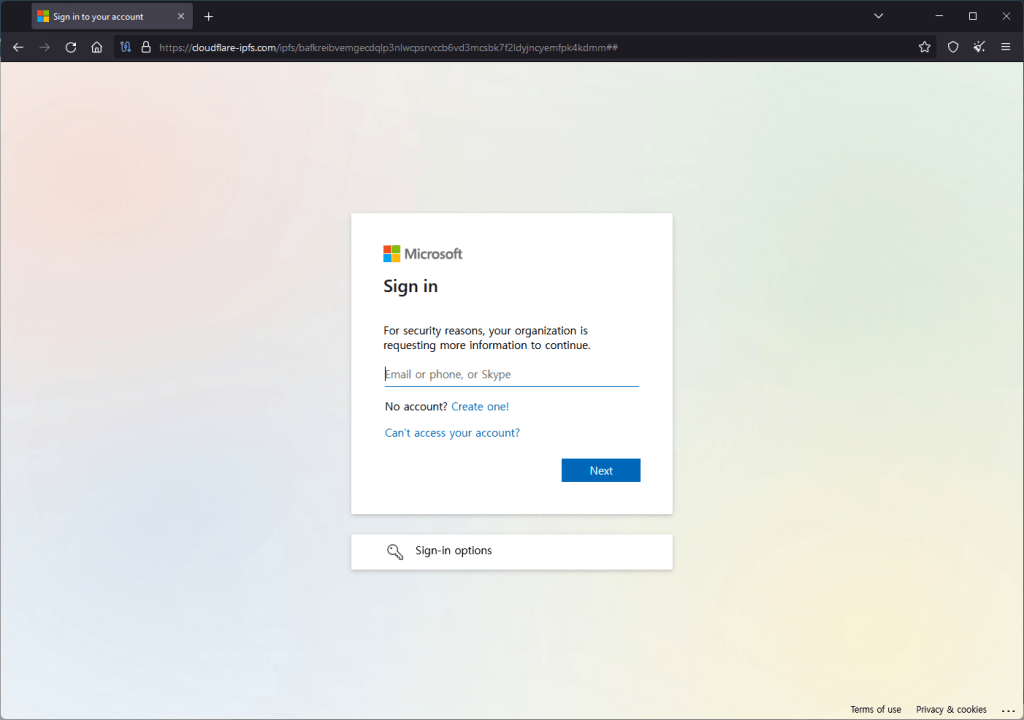
The site presents itself as a classic file remote drive that requires you to open a document. By clicking on the button, your local file browser (explorer or finder) opens, showing a well-presented artifact that is not very clear for an inexperienced user, interface.
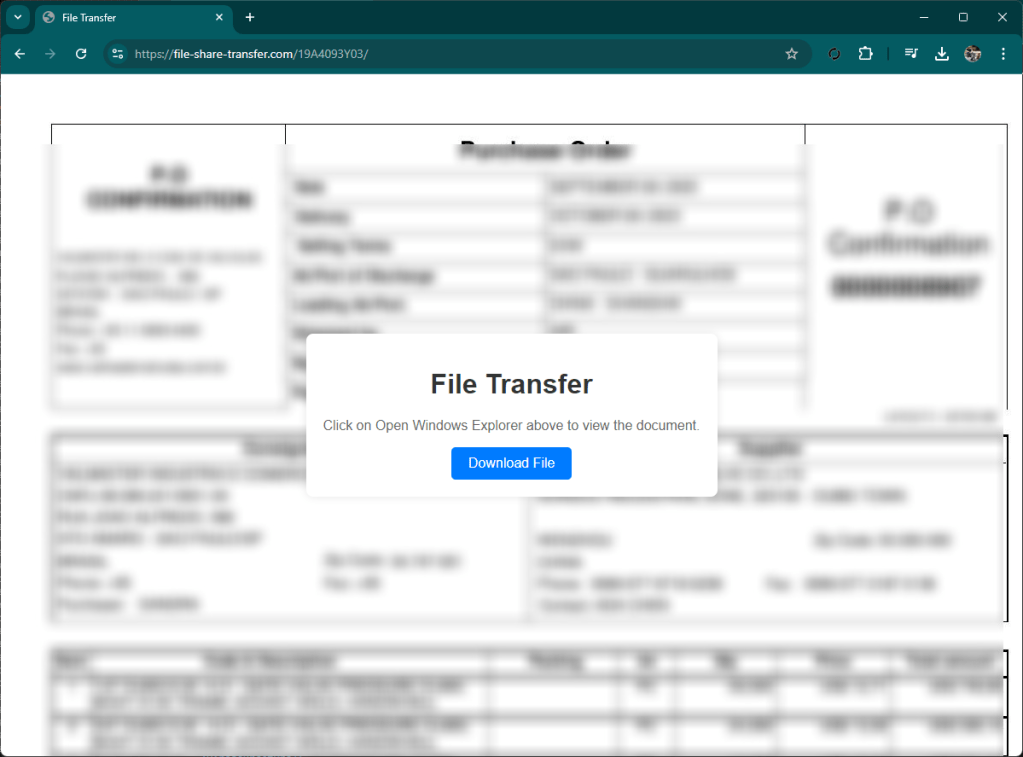

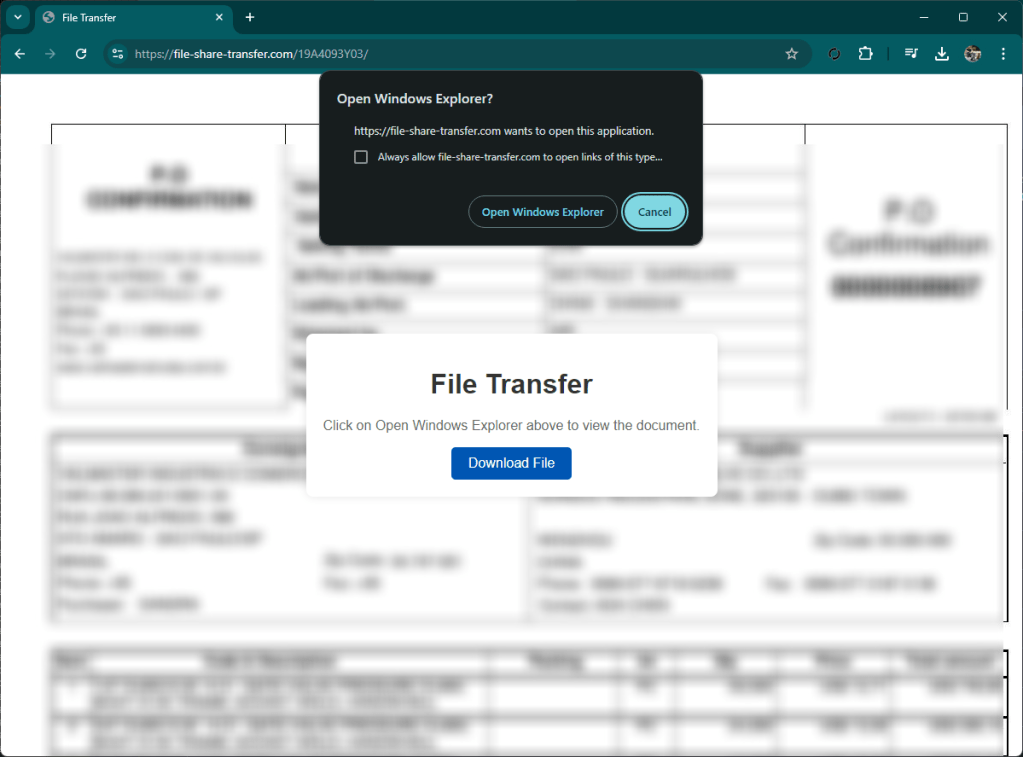
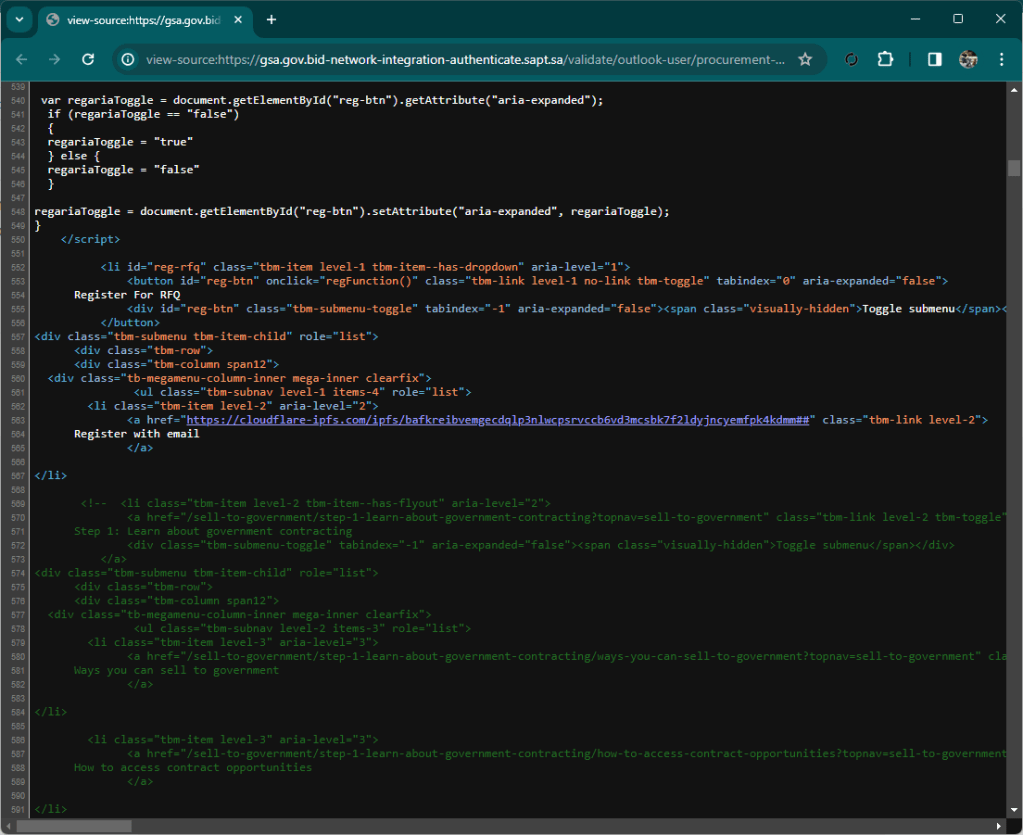
At first glance, in fact, you might think that the document presented is a local document, while in fact it is a link to a well-disguised remote file.
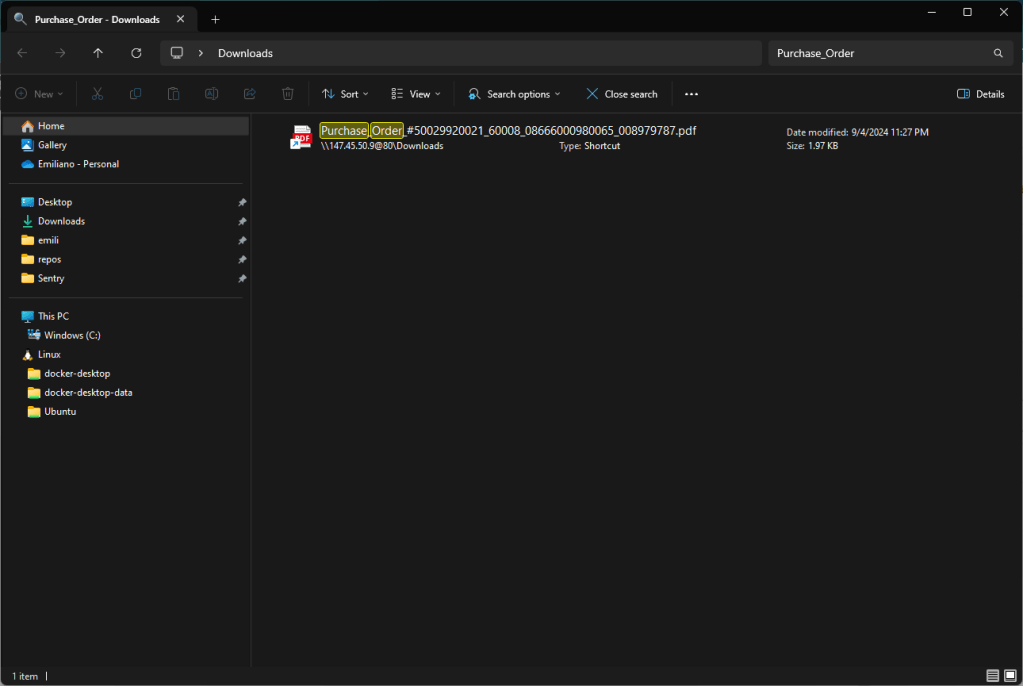

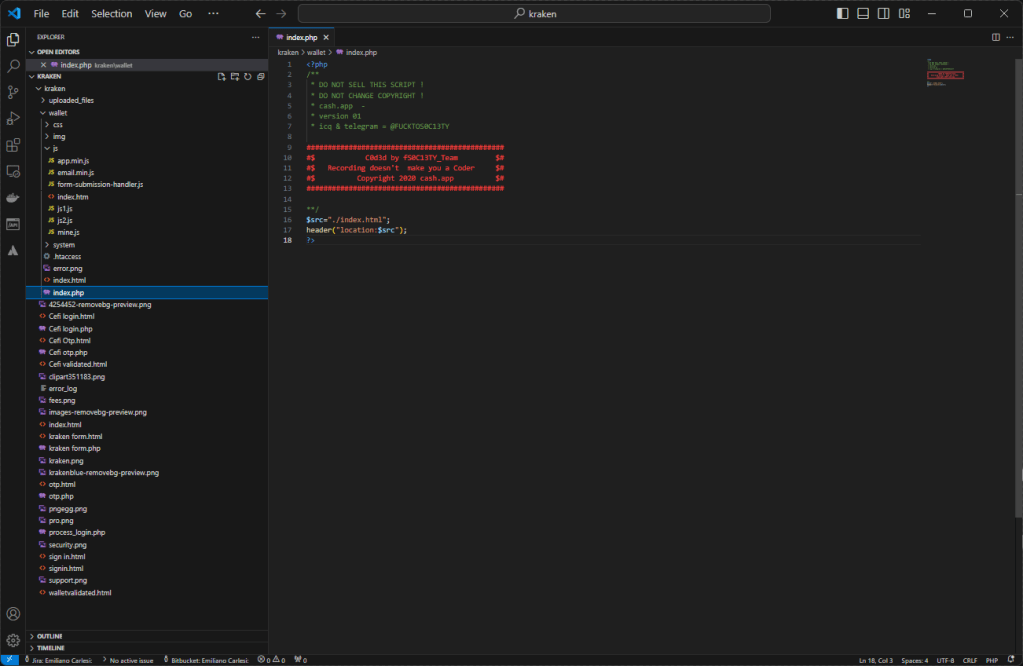
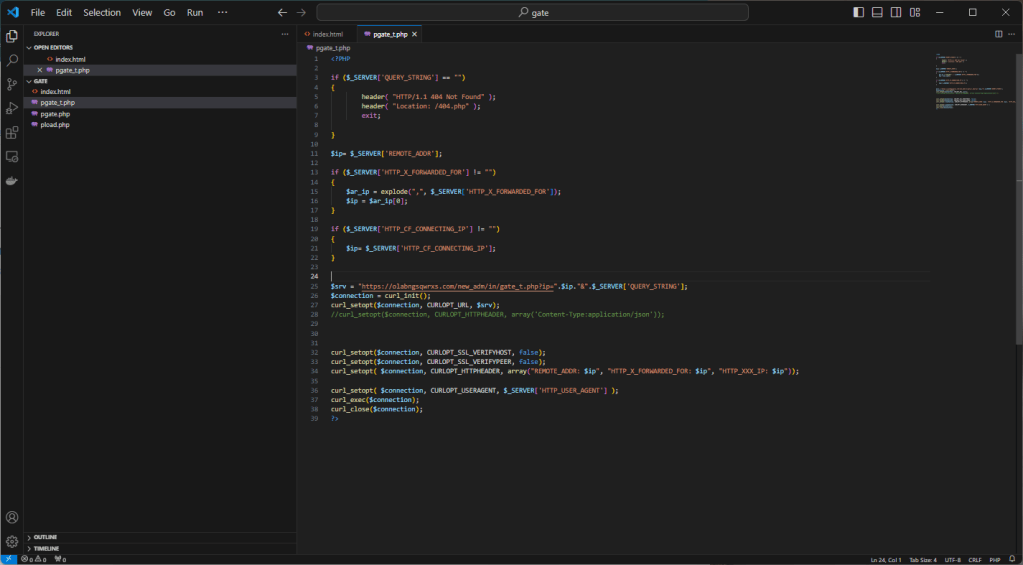
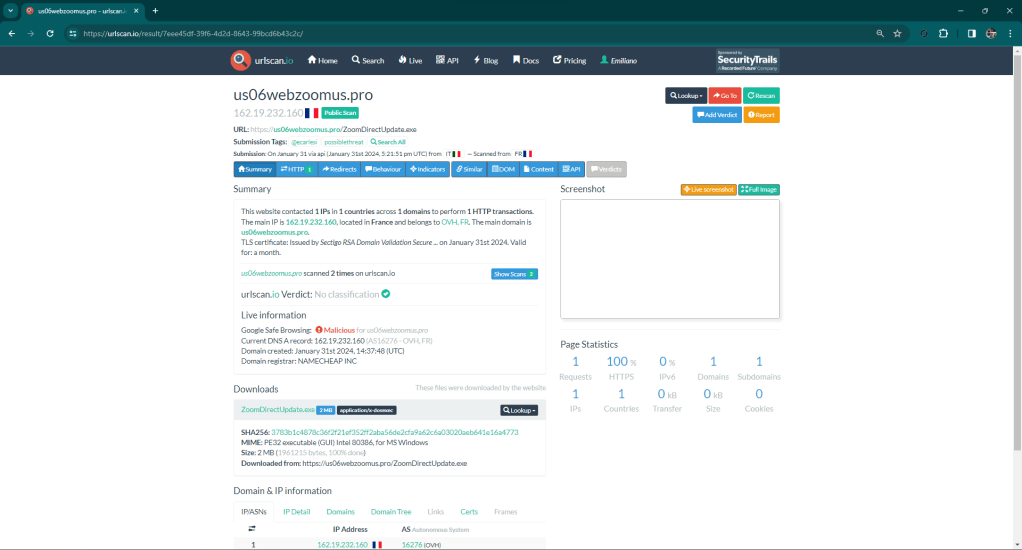
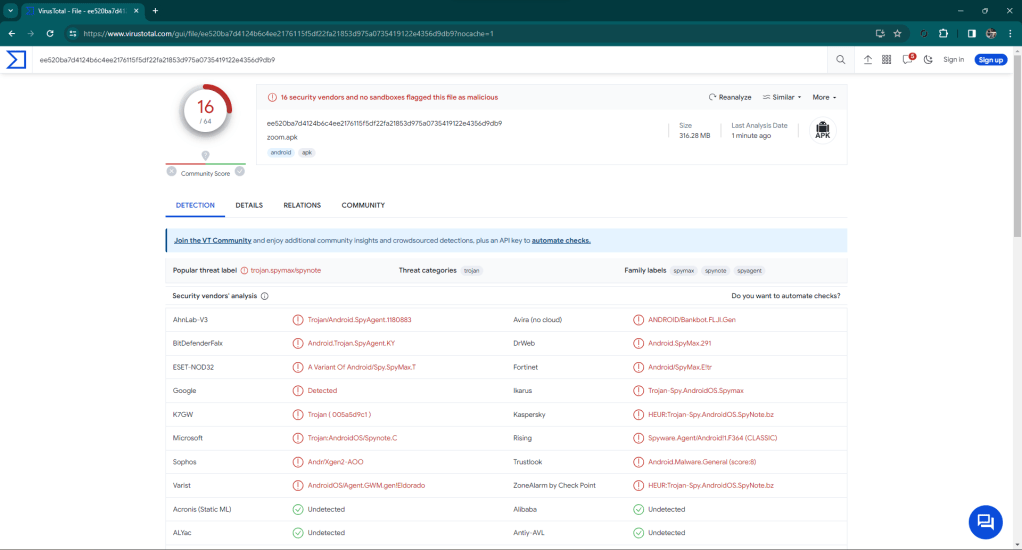
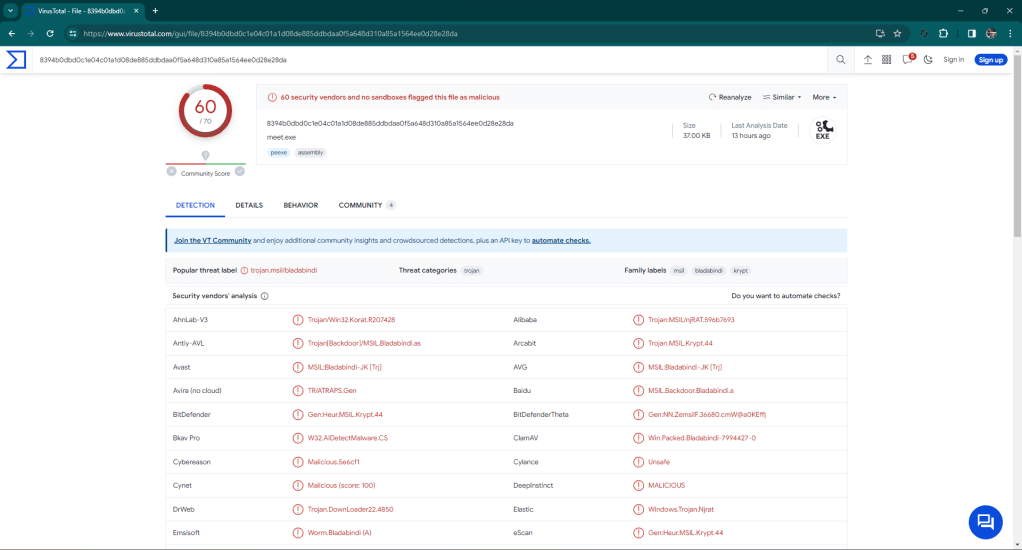
By proceeding, a link file is downloaded locally that references a malware that is downloaded from Alibaba’s cloud.
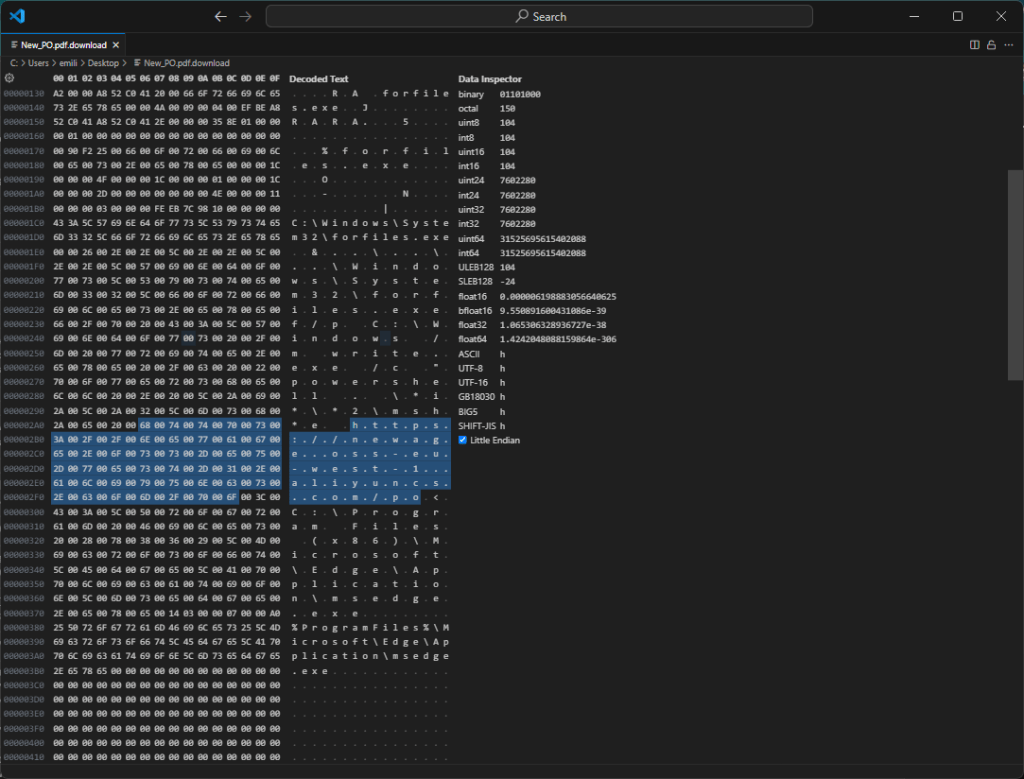
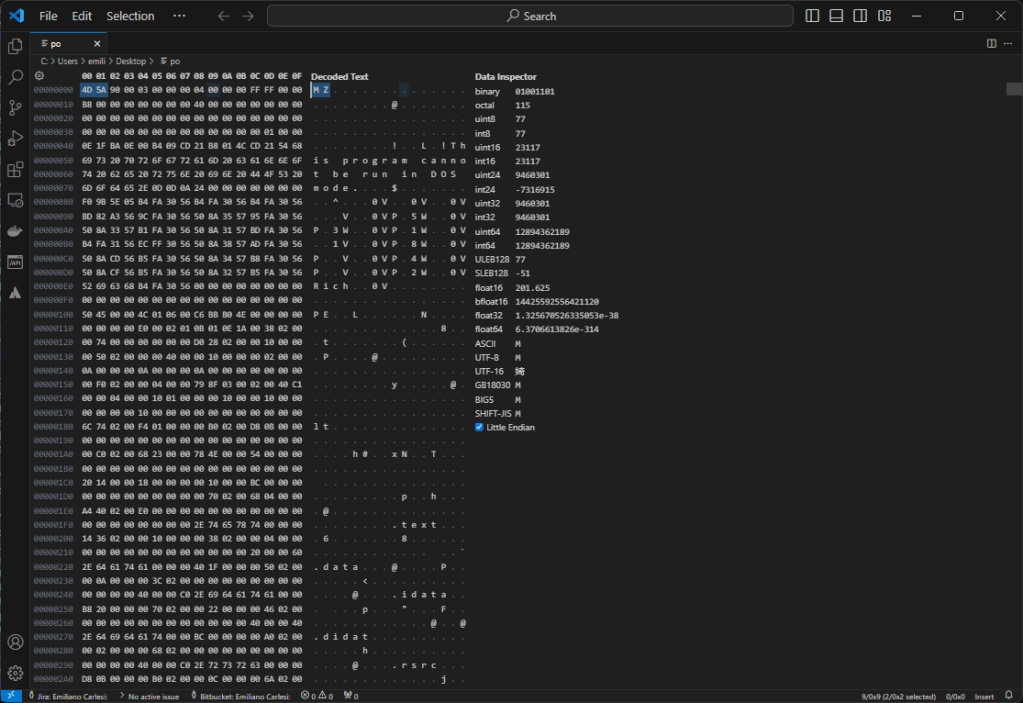
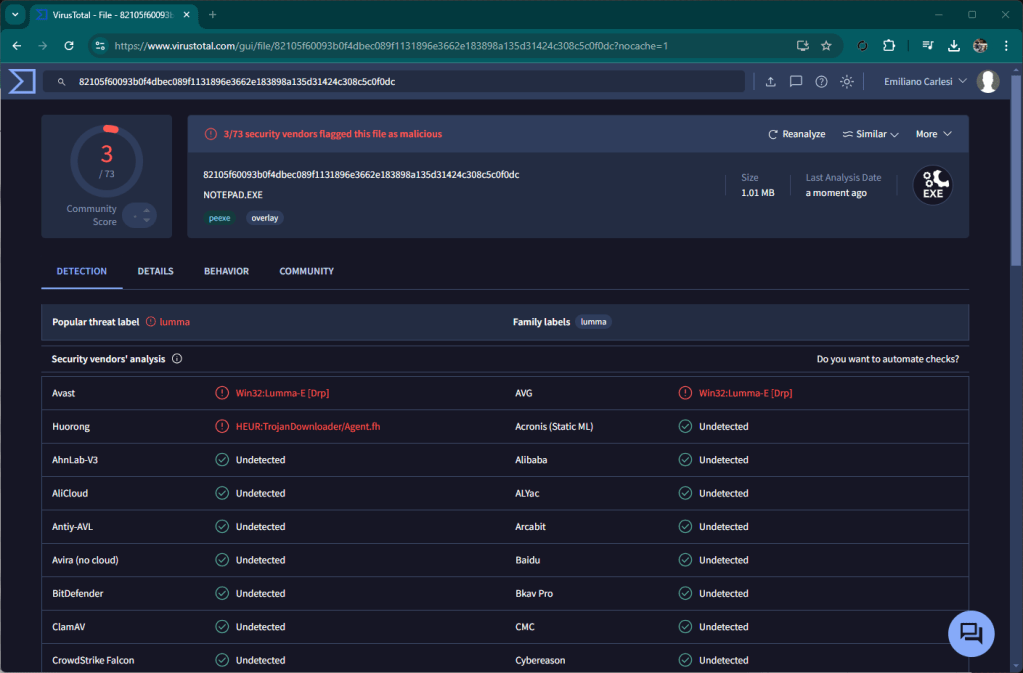
This attack is done fairly well, nothing particularly advanced but overall it is very fluid and credible. Performed towards a reality with little expertise it certainly has a good chance of success.
This leads us to understand how it is necessary to improve security at the infrastructure level because an attack like this will hardly be discovered by an average user. In my opinion, a more stringent sandbox on the browser and a more precise analysis would be necessary. My Chrome during this analysis did not highlight anything, the same for Defender. There is still a lot of work to do to make everyone safe.


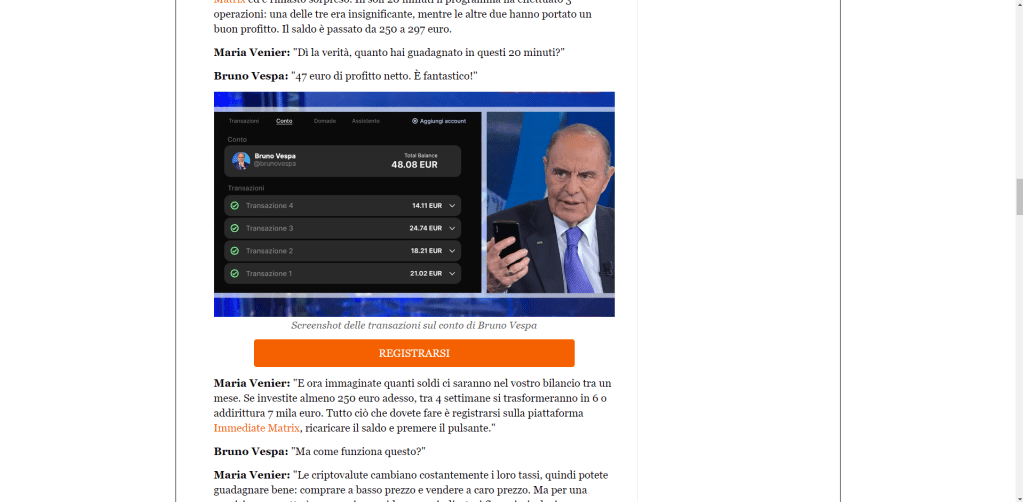













You must be logged in to post a comment.