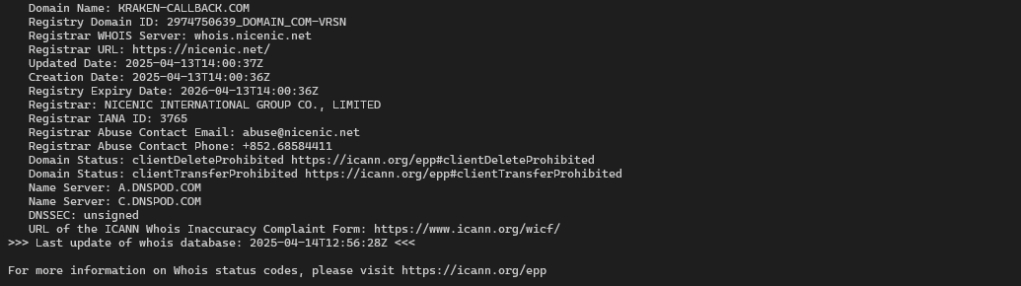
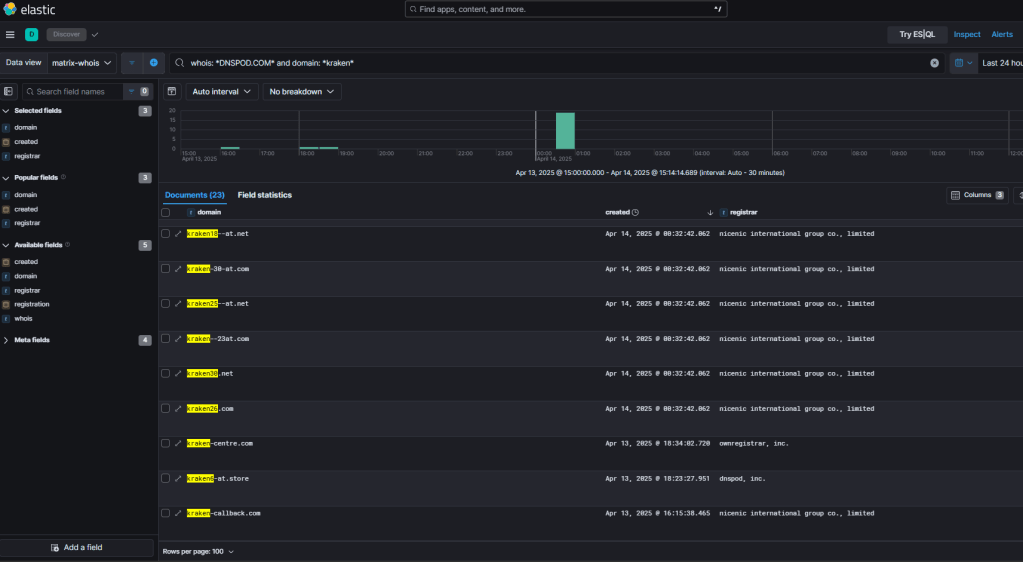
Looking at what ends up in the Matrix network I noticed a kit that targets Kraken customers.

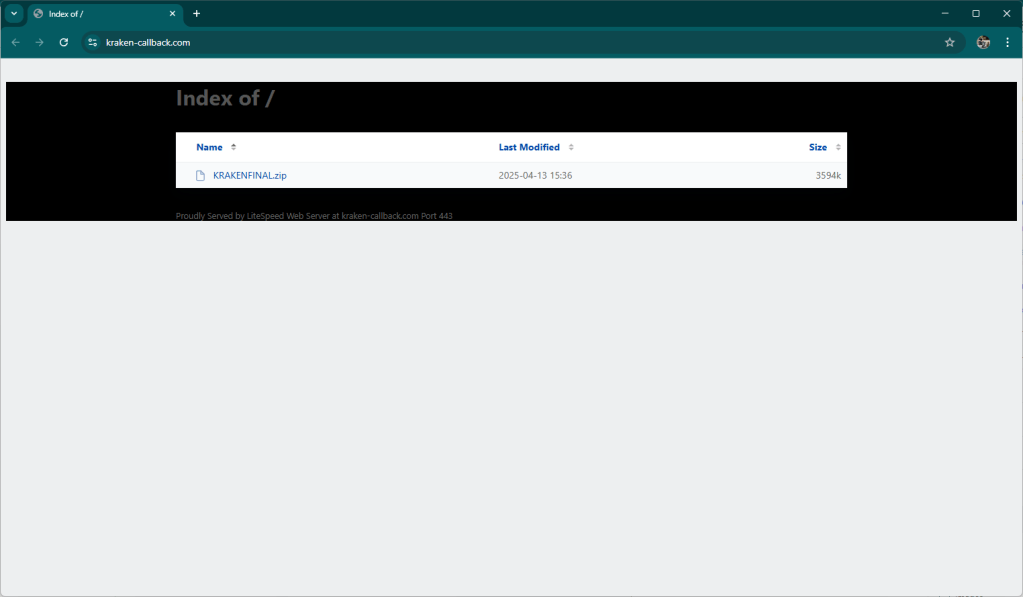
As usual, the victim is frightened with an alleged compromise of their account.
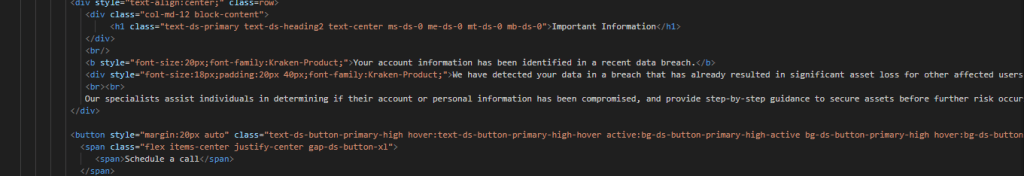
The interesting aspect of this kit is that instead of asking the victim to enter their wallet details, the application suggests the victim to schedule a phone meeting. The user is asked to leave their phone number and is even provided with an .ics file with the appointment details, so that the victim remembers not to make other commitments 😀
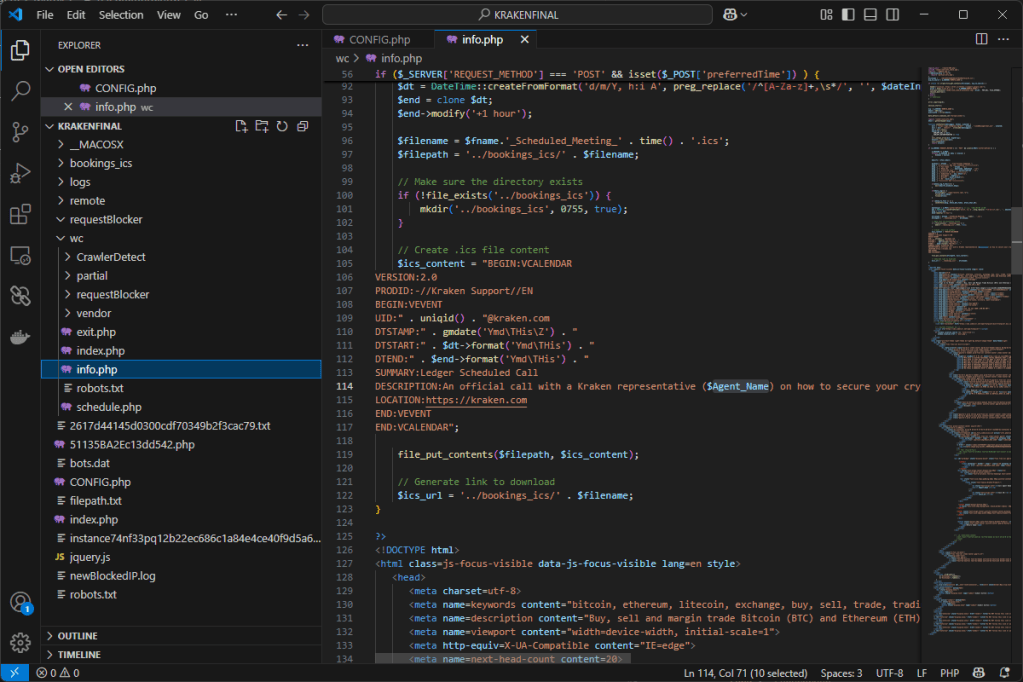
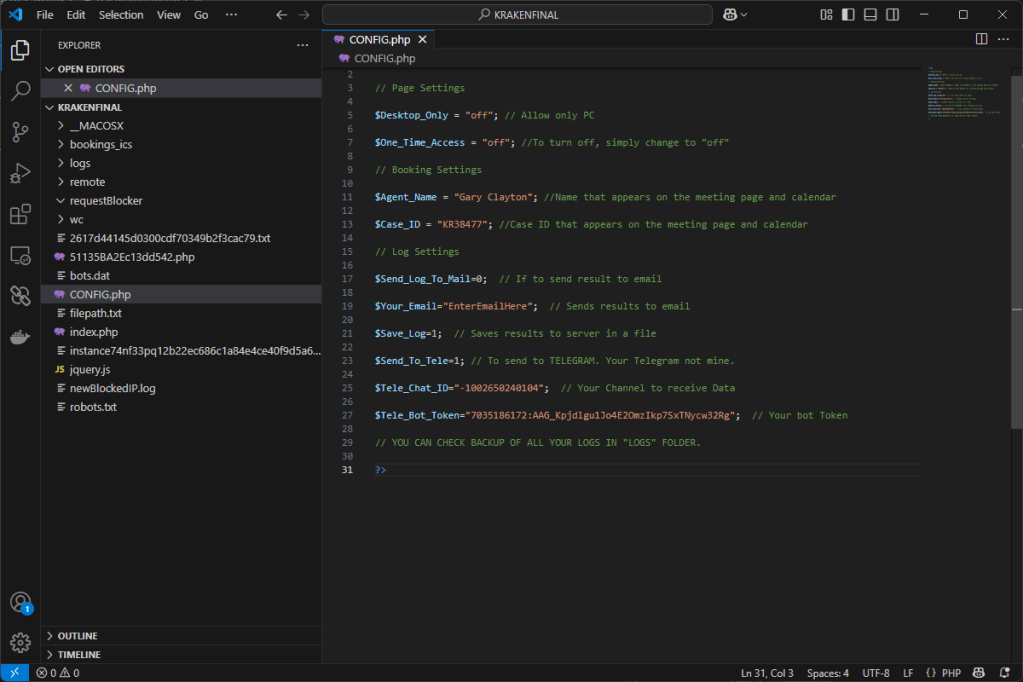
The user data is sent to a Telegram bot as usual.
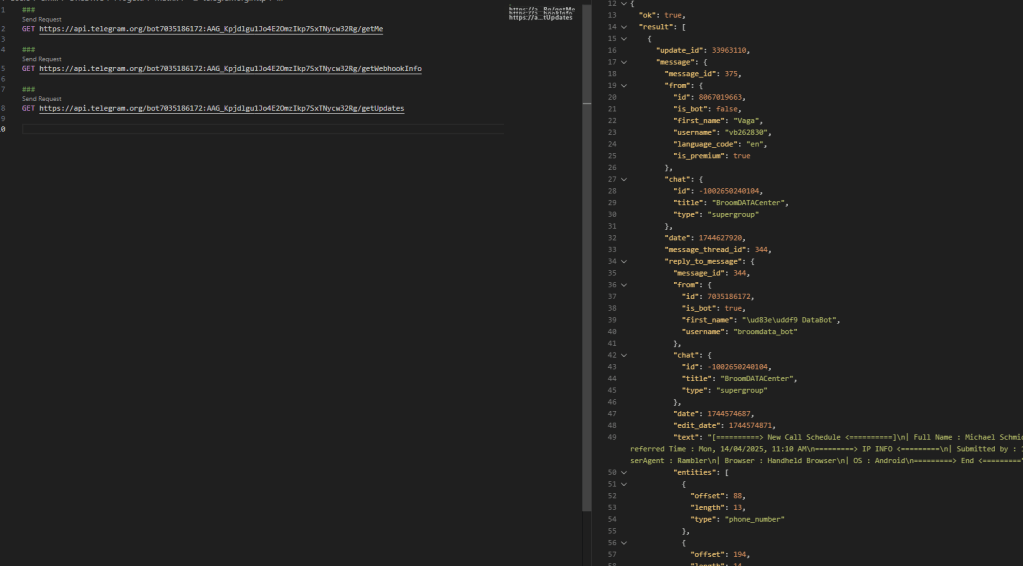
Looking for updates received from bots we find several messages waiting to be read by the fraudster. Since the domain where we found the kit does not yet have the kit online, it means that there are other sites with the kit already in operation.
Searching Elastic for domains with “kraken” in their names that are managed by the same DNS server (dnspod.com) brought up several other domains including kraken-centre.com which of course has the kit already online.