Given that the Iranian regime disgusts me, as does every theocracy, I dedicate time to this kit because it has interesting features and because I think that we all owe solidarity to the Iranian population, persecuted by a fascist regime.
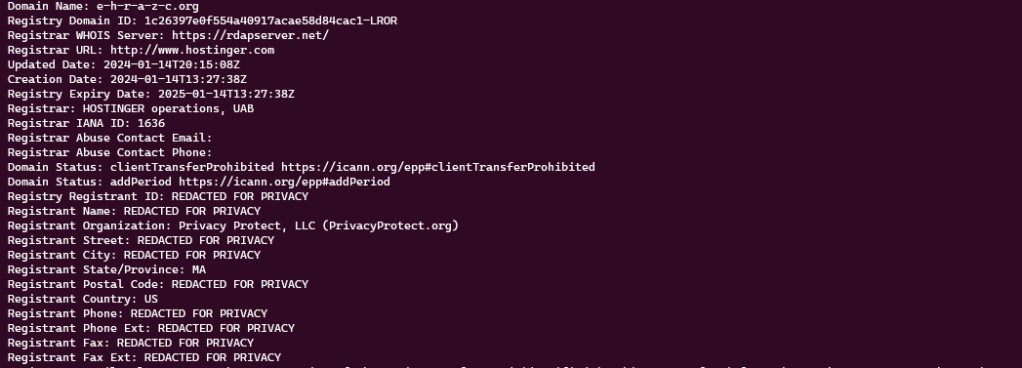
After this introduction, let’s move on to this kit. Matrix downloaded it from the e-h-r-a-z-c[.]org domain around 9pm today (January 14, 2023). The domain was registered via hostinger.com
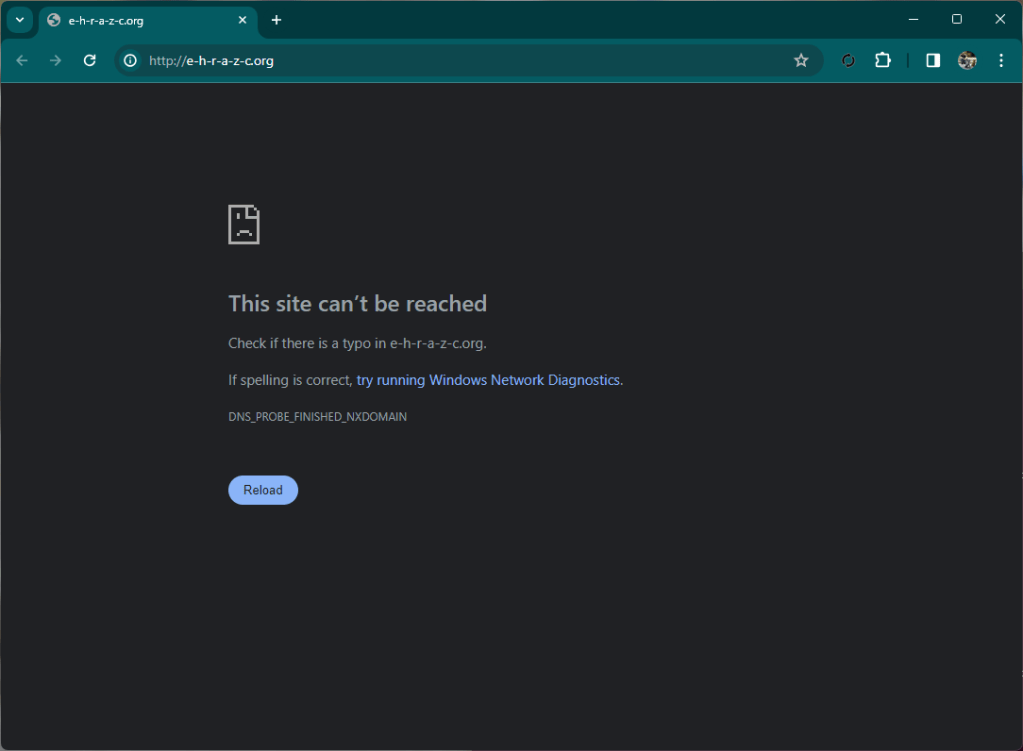
At the time of writing this article (about two hours have passed since the kit was found) the web site is inactive.
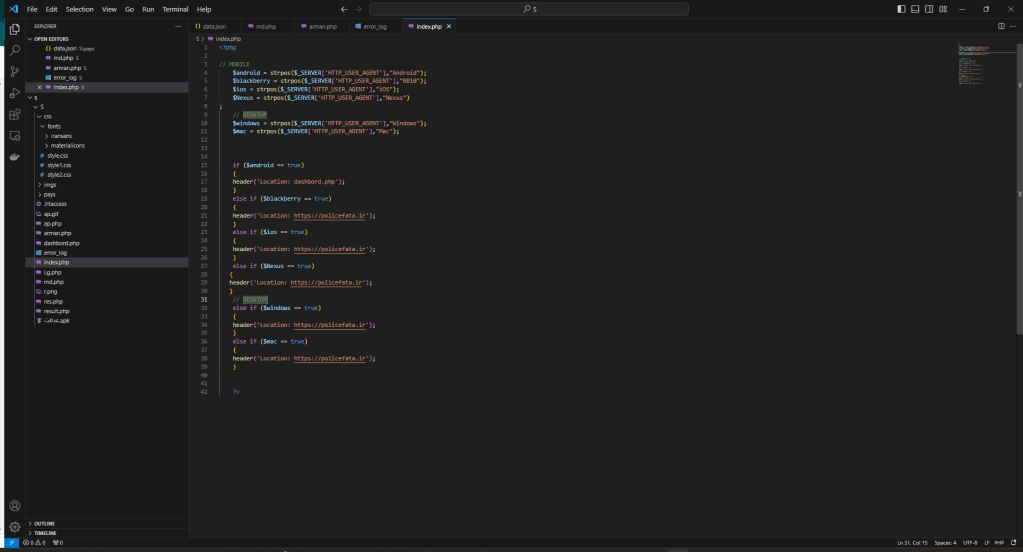
Inside the kit there are the PHP sources that make up the phishing site and a malware for Android.

The kit targets customers of several banks.
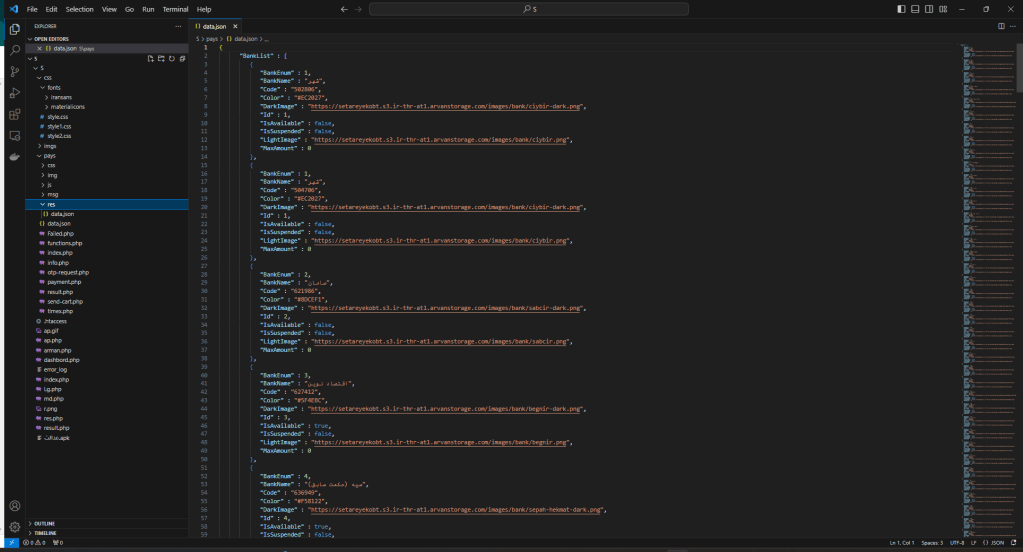
In the PHP sources we find the token to which the stolen credentials are sent.
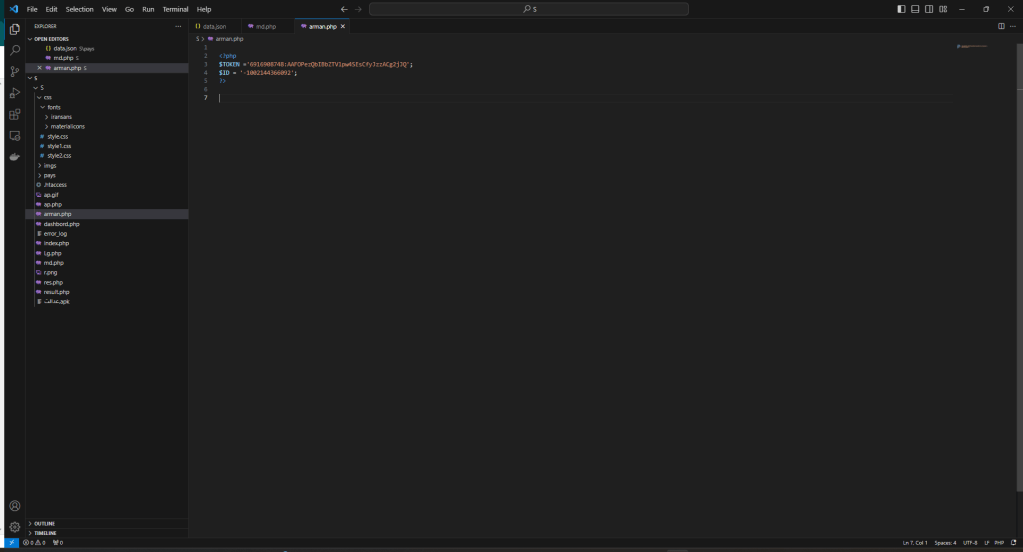
The site is not listed on urlscan.io because at the time of the notification the site was already offline. I can say we downloaded the kit at the last second 🙂
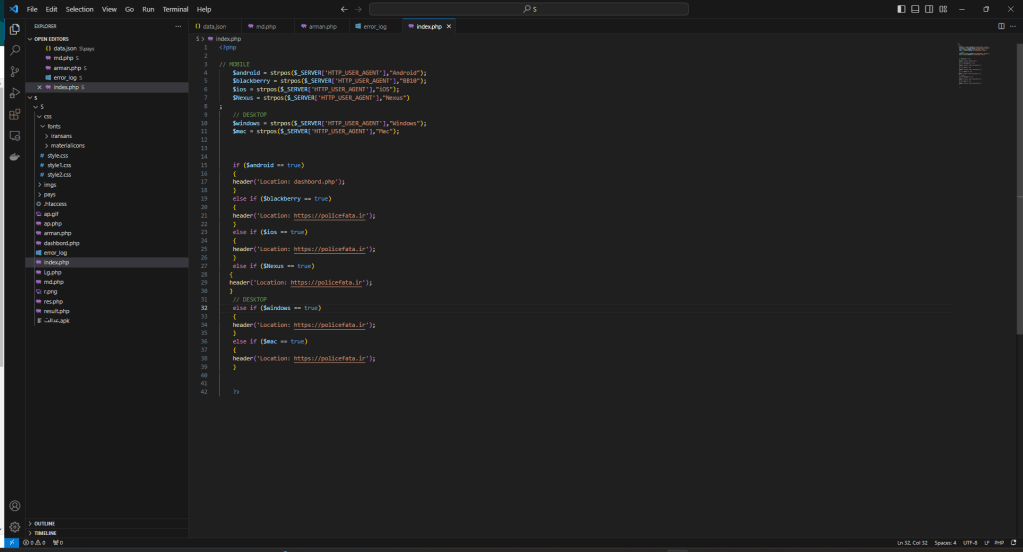
The main goal of the attack was to install malware. This can also be deduced from the cloaking mechanism which redirects all non-Android devices to the cyber police website which deals with cyber security.